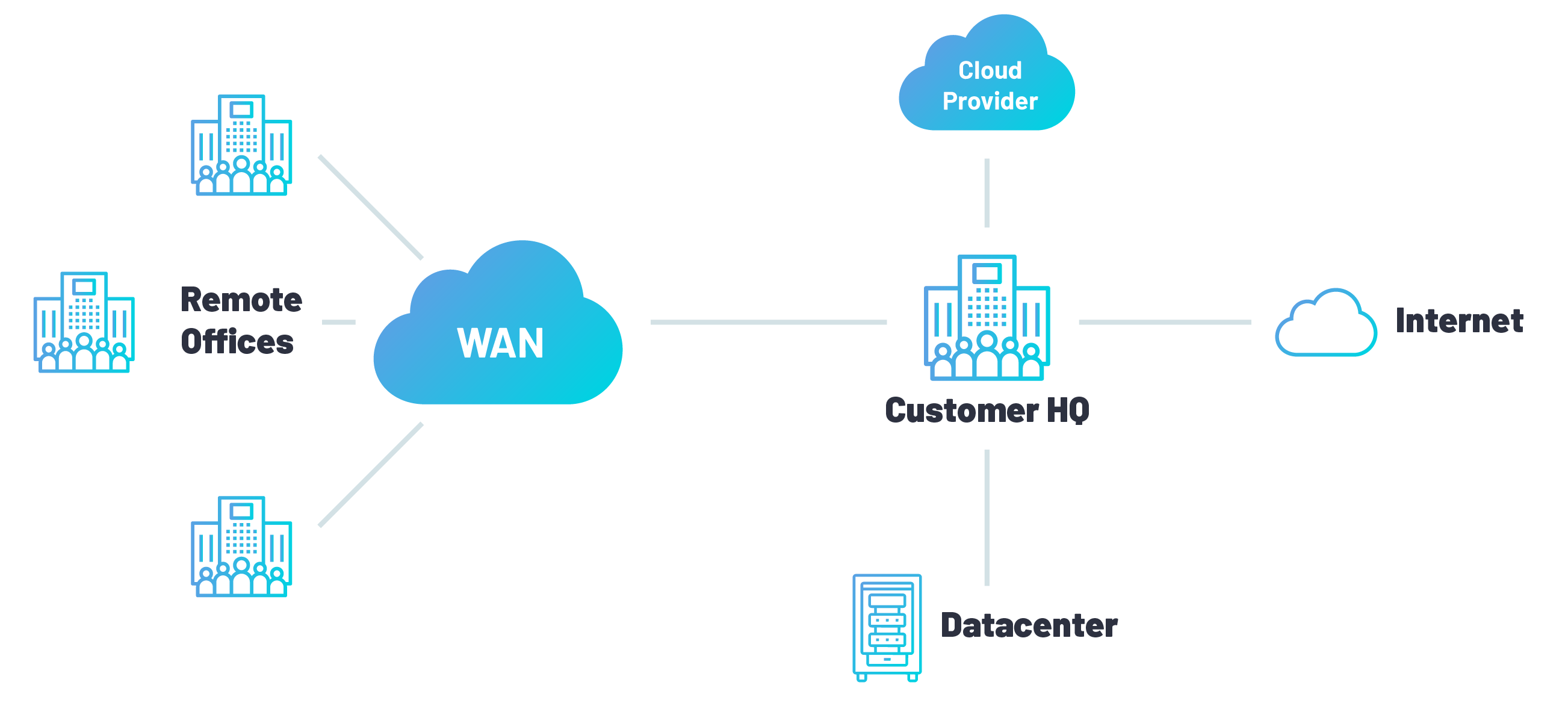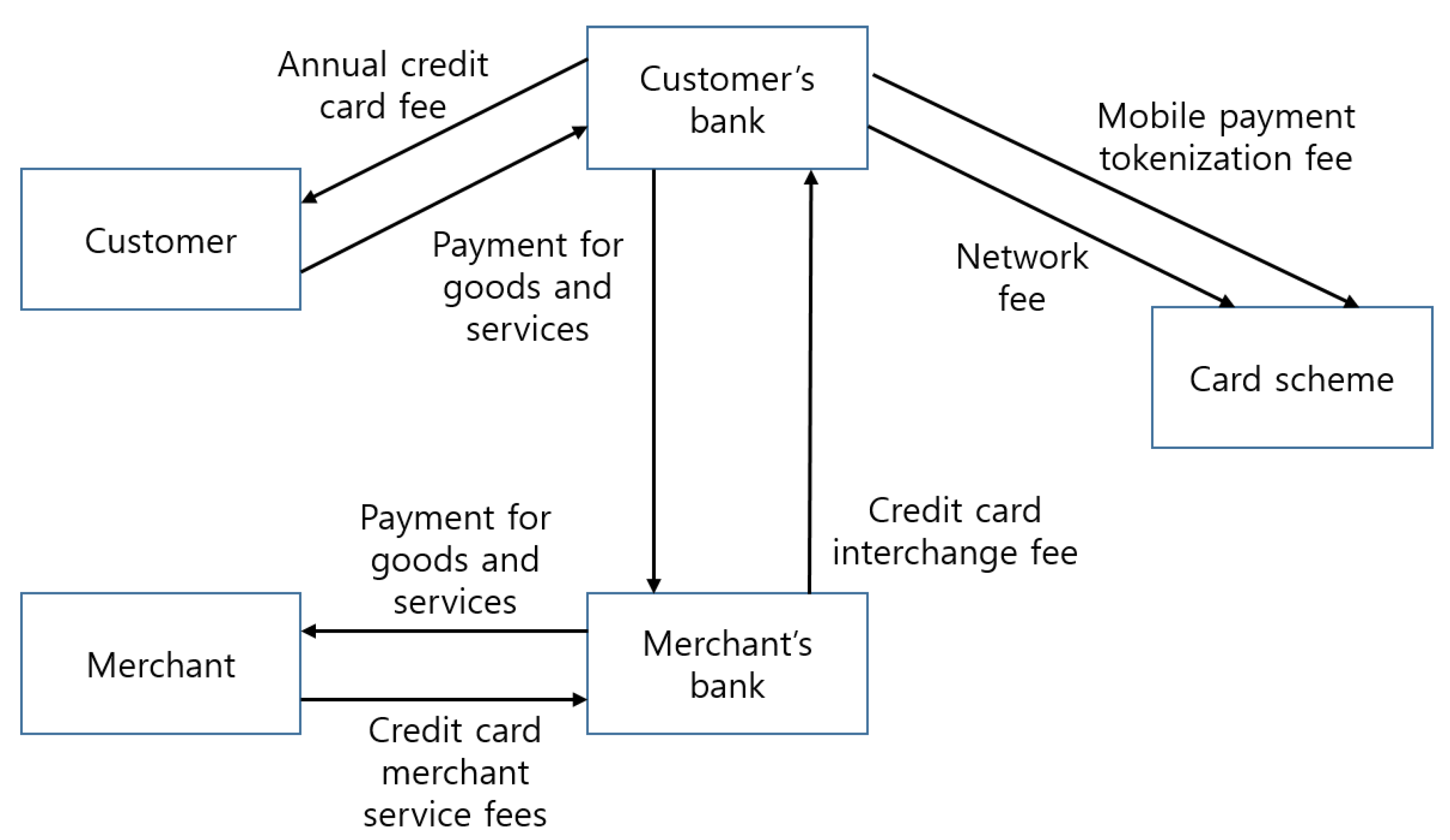
Symmetry | Free Full-Text | Blockchain Security in Cloud Computing: Use Cases, Challenges, and Solutions
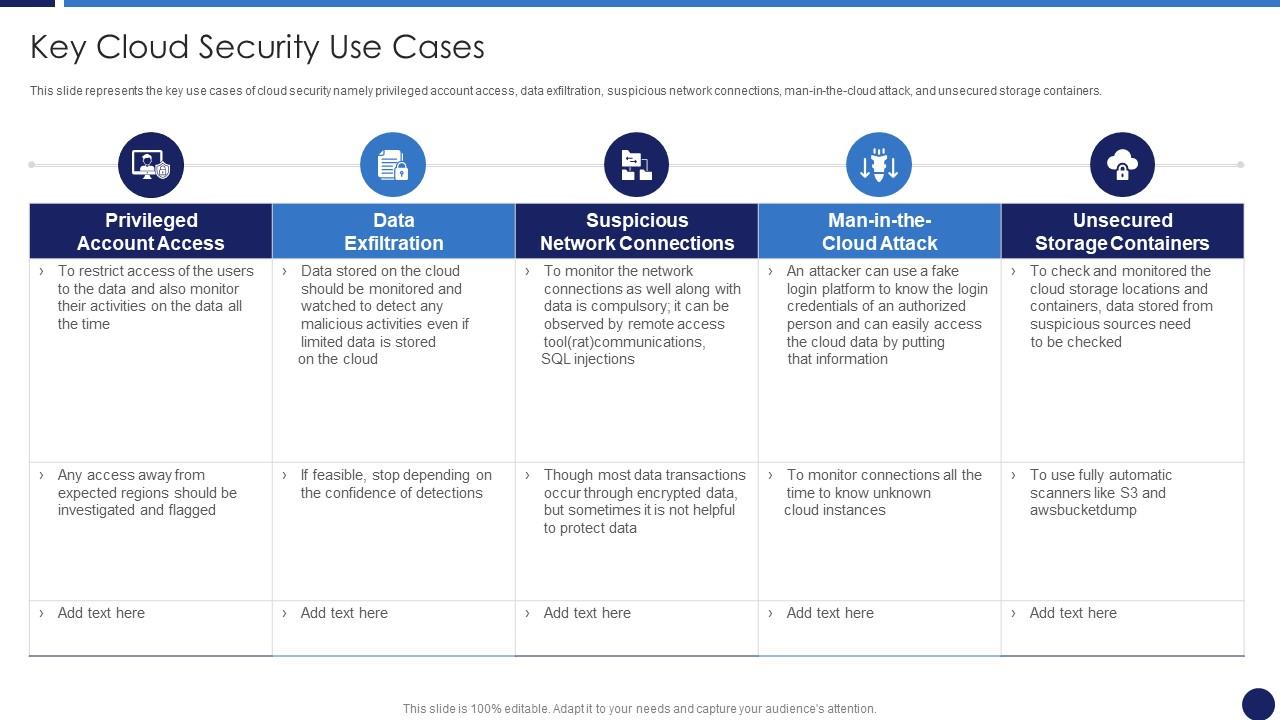
Key Cloud Security Use Cases Cloud Data Protection | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
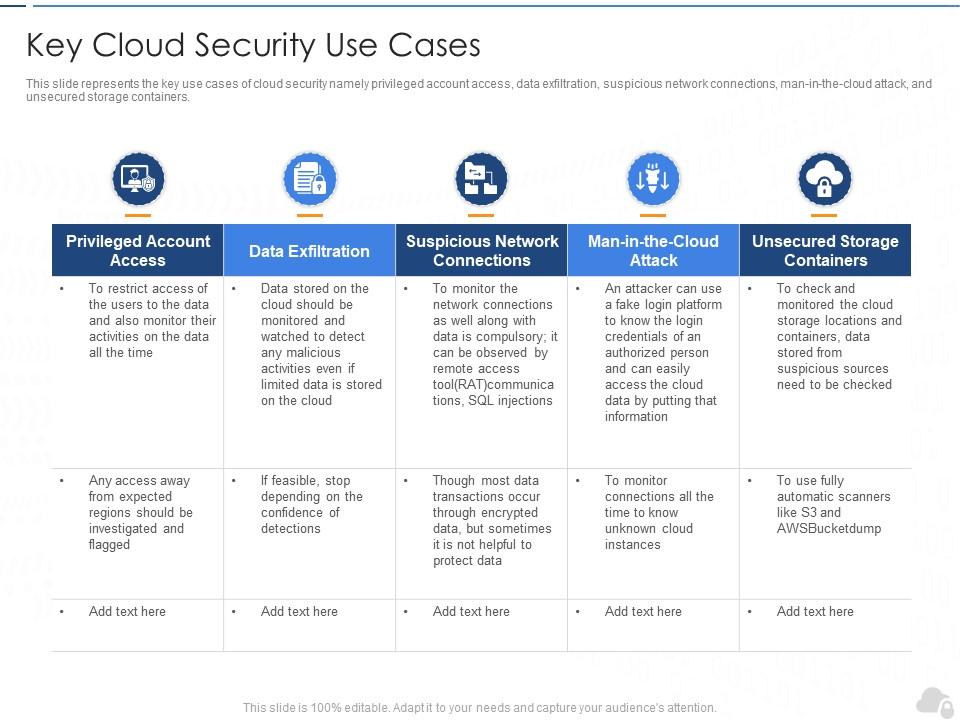
Key Cloud Security Use Cases Cloud Security IT Ppt Summary | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

From my Gartner Blog - Developing and Maintaining Security Monitoring Use Cases - Security Boulevard