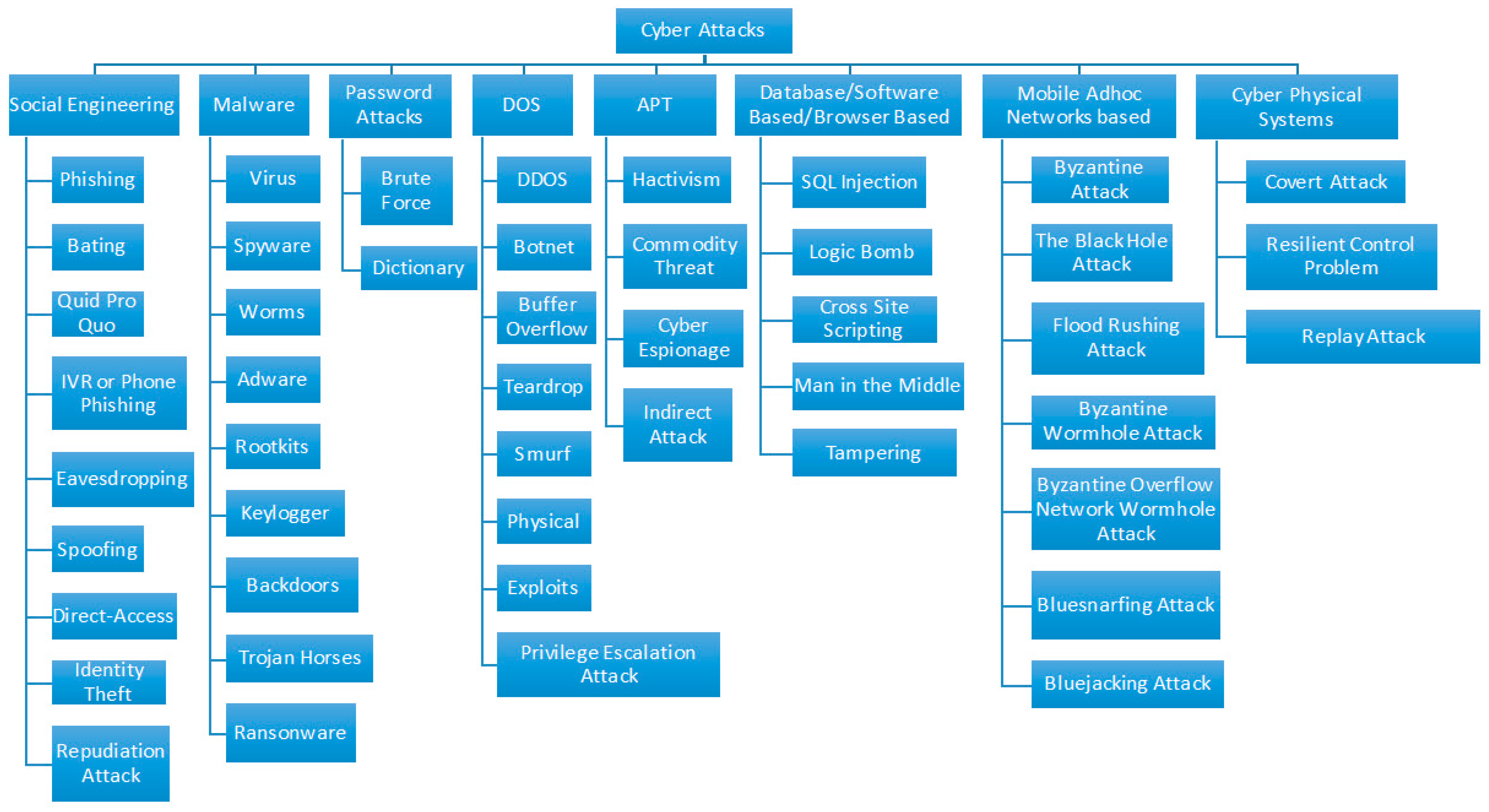
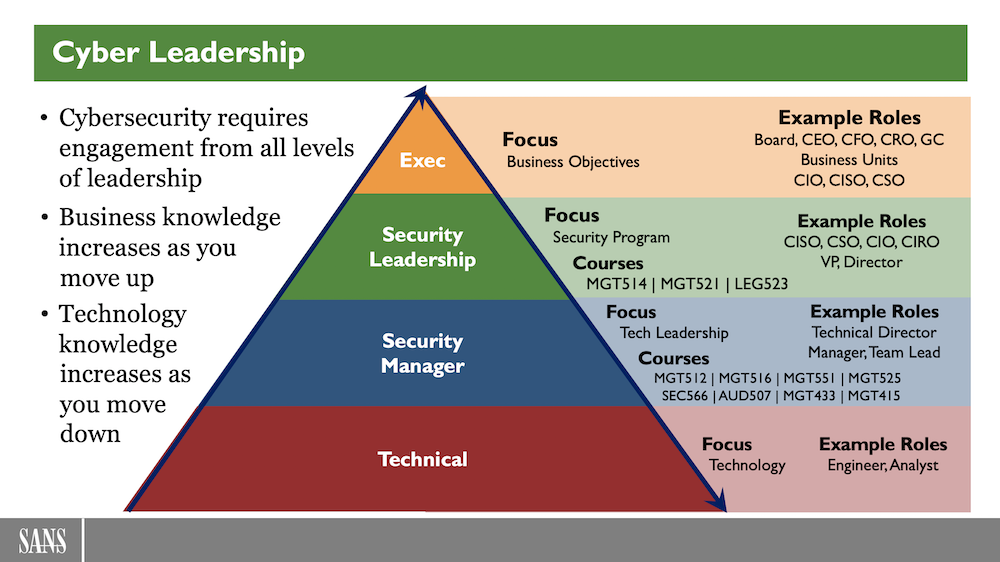
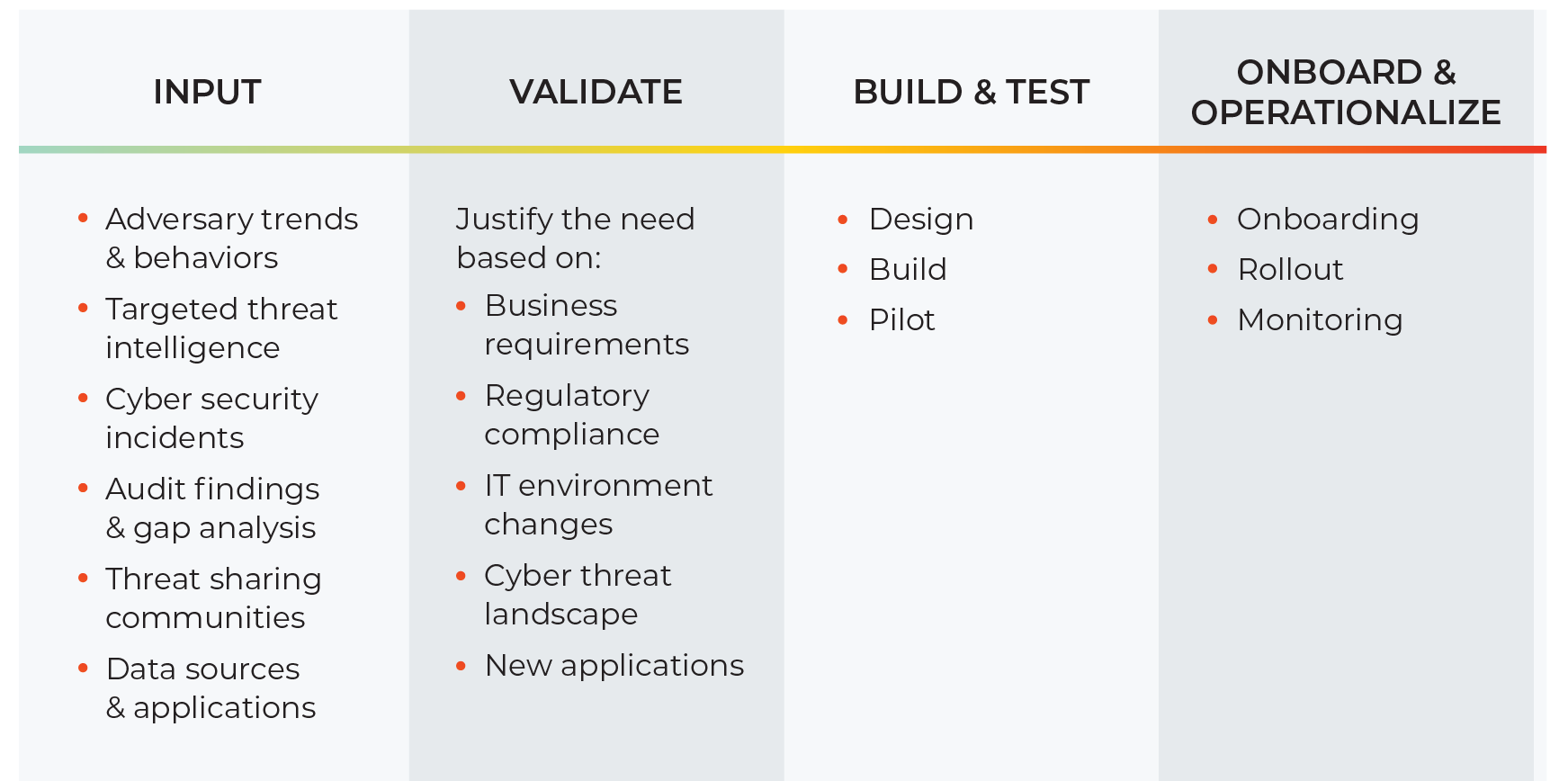
The Cyber Security Hub™ в Twitter: „#Blockchain Use Cases #Fintech #Bitcoin #IoT #Cloud #cloudcomputing #tech #security #infosec #cybersecurity #ITsecurity #NetworkSecurity https://t.co/cpSTRM1MTJ“ / Twitter
Cyber Attack Case Study Ppt Powerpoint Presentation Visuals | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Top Three Use Cases for AI in Cybersecurity | Data Center Knowledge | News and analysis for the data center industry