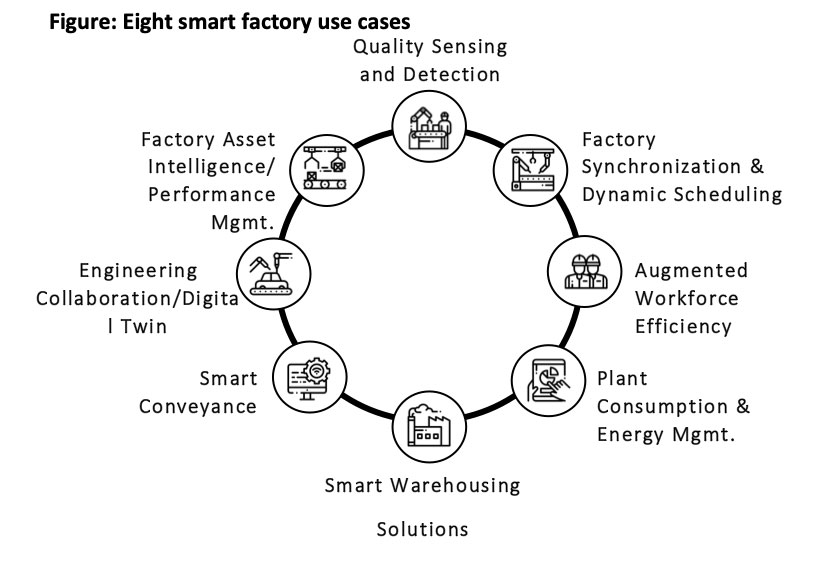
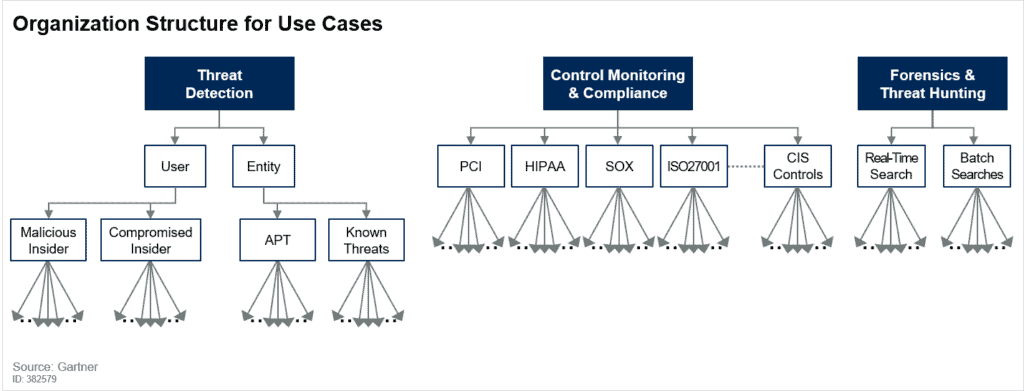
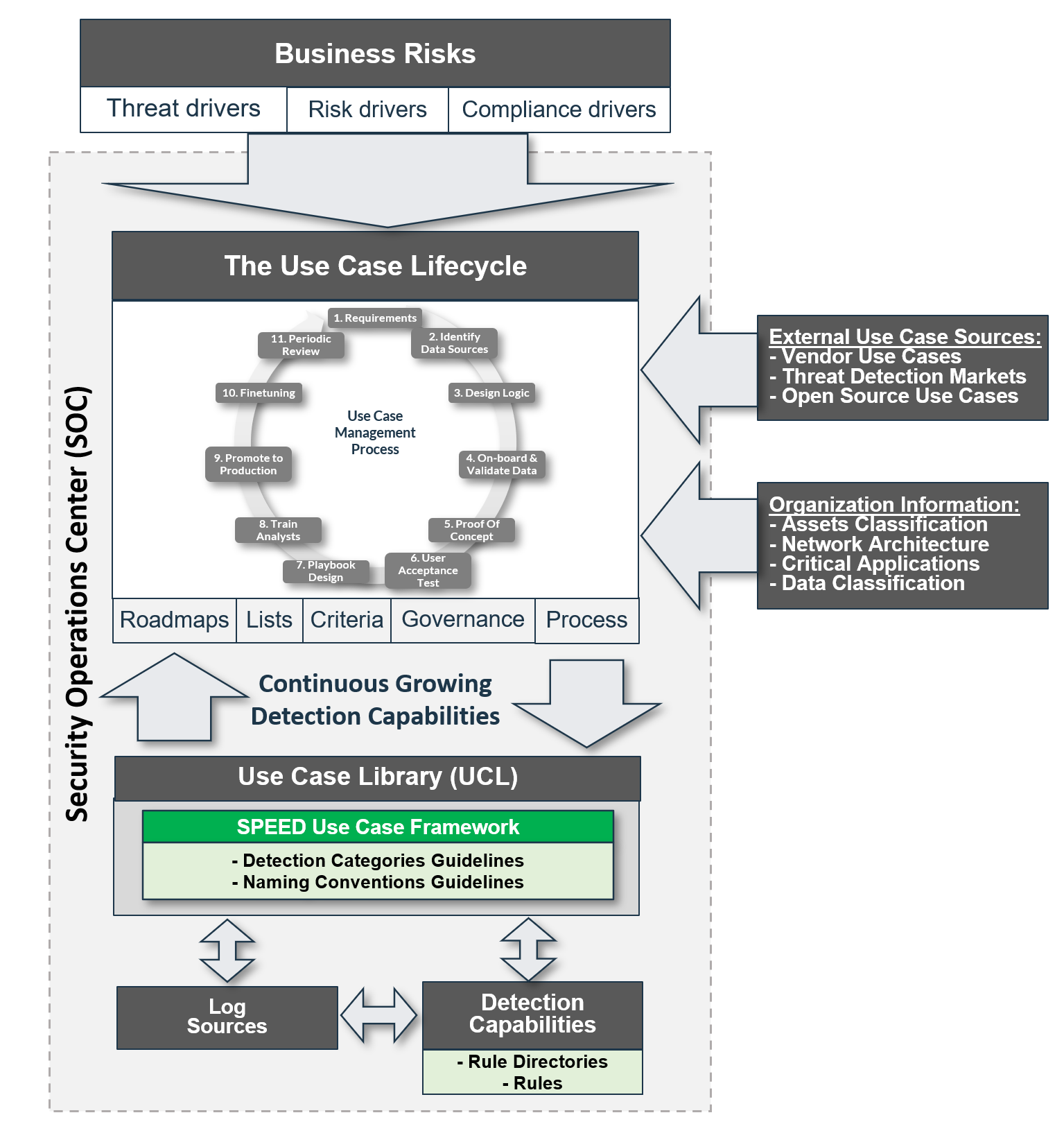
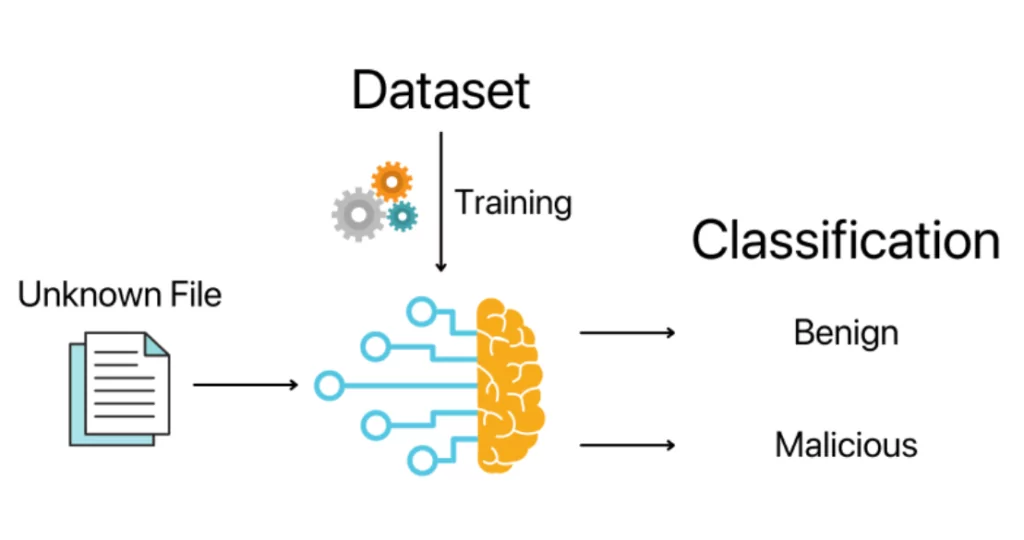
![PDF] A Use Case in Cybersecurity based in Blockchain to deal with the security and privacy of citizens and Smart Cities Cyberinfrastructures | Semantic Scholar PDF] A Use Case in Cybersecurity based in Blockchain to deal with the security and privacy of citizens and Smart Cities Cyberinfrastructures | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/894422818808260bae2c8bf6a63ea61deb52686c/3-Figure2-1.png)
PDF] A Use Case in Cybersecurity based in Blockchain to deal with the security and privacy of citizens and Smart Cities Cyberinfrastructures | Semantic Scholar
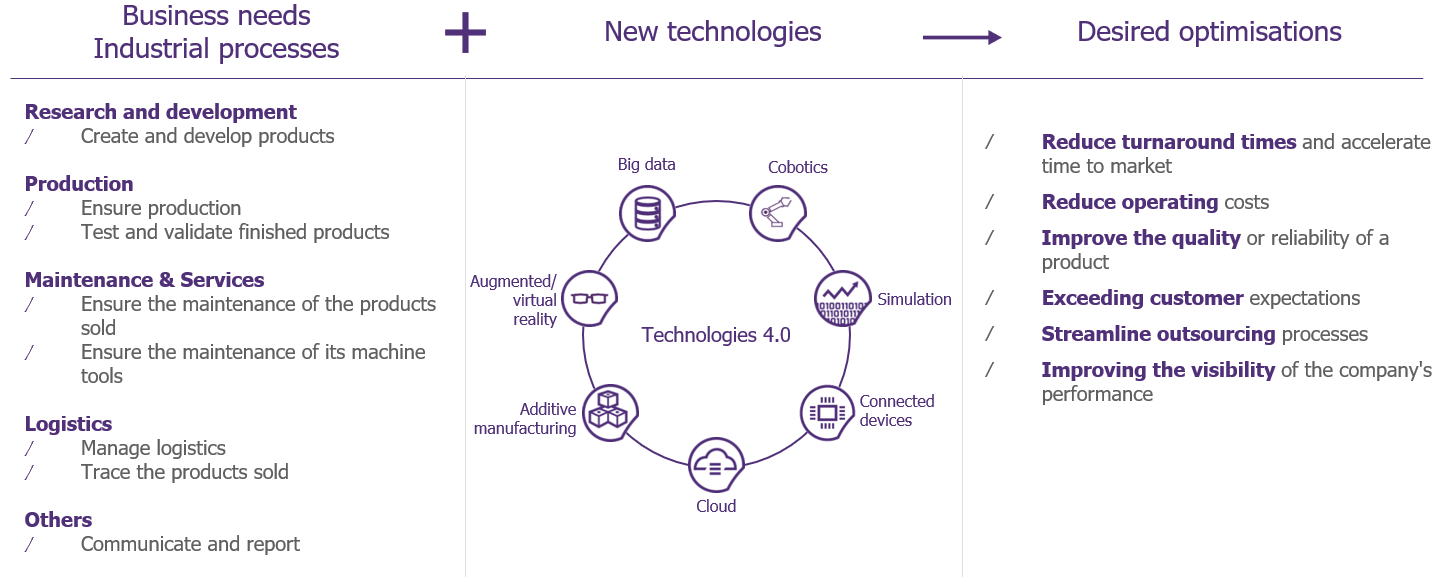
Industrial Cybersecurity in the Age of Industry 4.0 : how can we secure these new use cases and support business projects? - RiskInsight