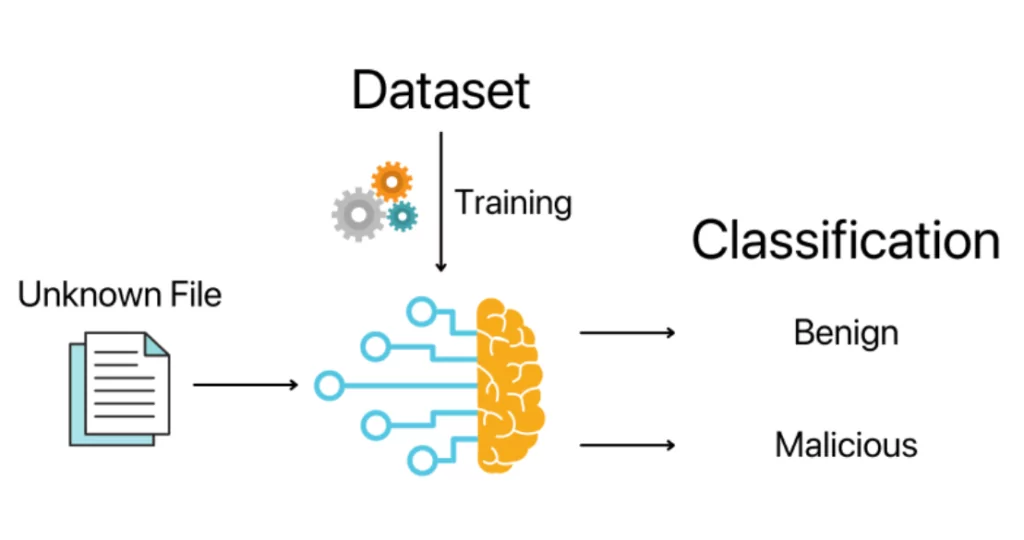
Cybersecurity leader sets a new record. Automates 90% of test coverage for rapid releases to counter new threats | Case Study
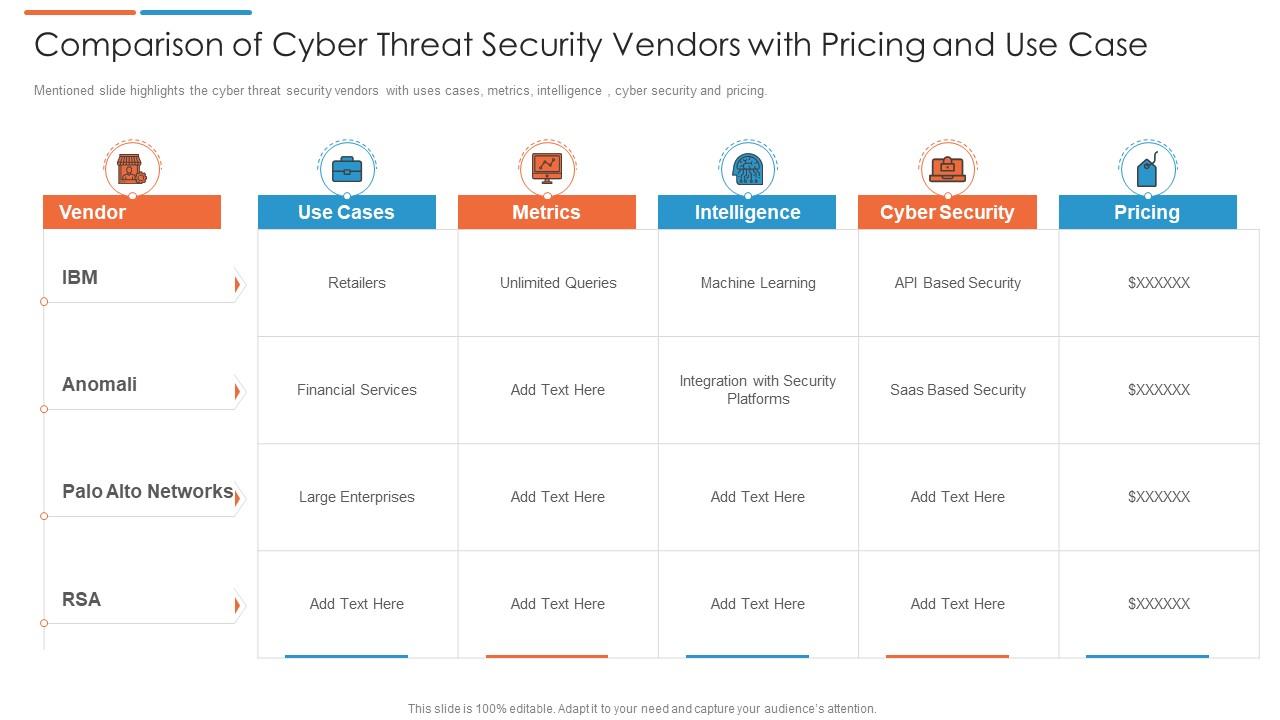
Comparison Of Cyber Threat Security Vendors With Pricing And Use Case | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
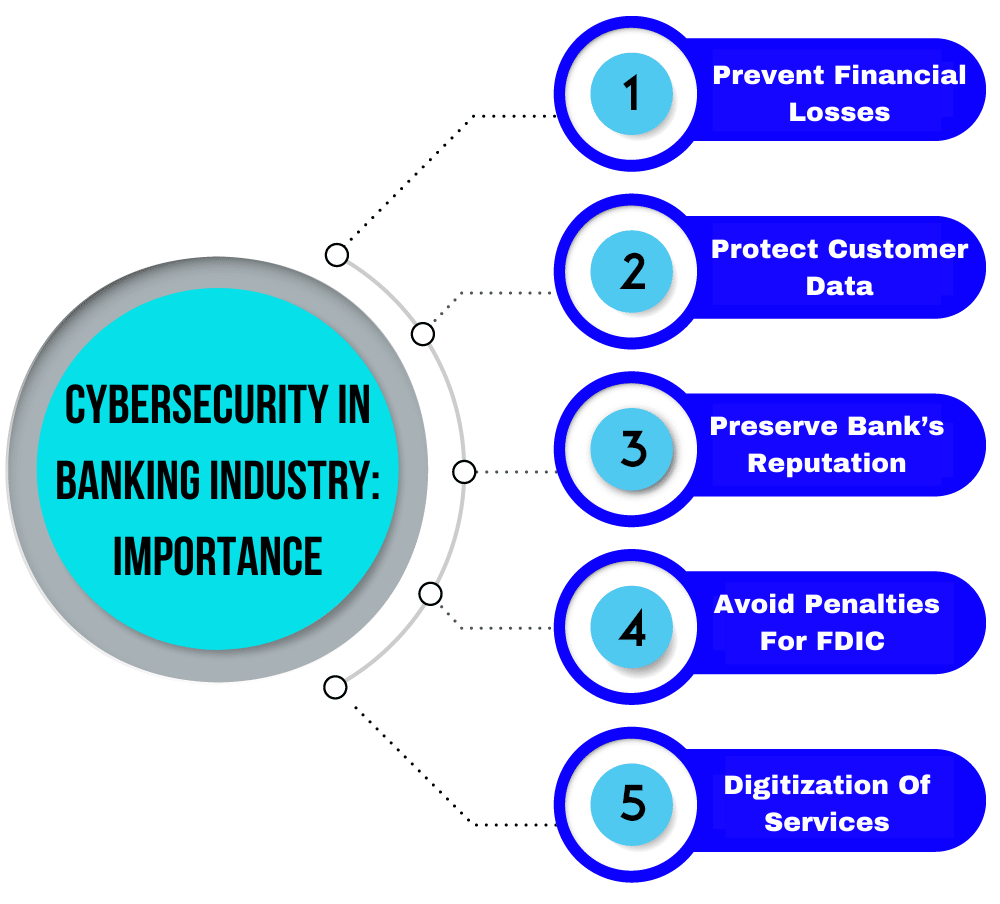
Cybersecurity in Banking Industry: Importance, Challenges, and Use-Cases - The European Business Review

Symmetry | Free Full-Text | Autonomous Vehicles: The Cybersecurity Vulnerabilities and Countermeasures for Big Data Communication

The Cyber Security Hub™ on Twitter: "#Blockchain Use Cases #Fintech #Bitcoin #IoT #Cloud #cloudcomputing #tech #security #infosec #cybersecurity #ITsecurity #NetworkSecurity https://t.co/cpSTRM1MTJ" / Twitter