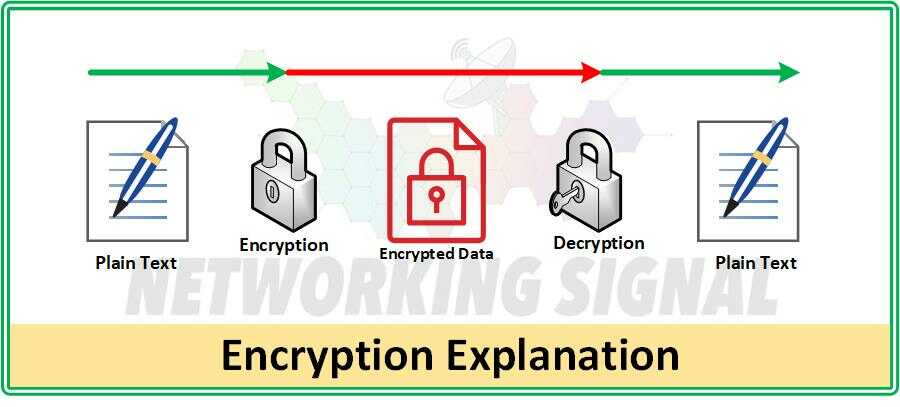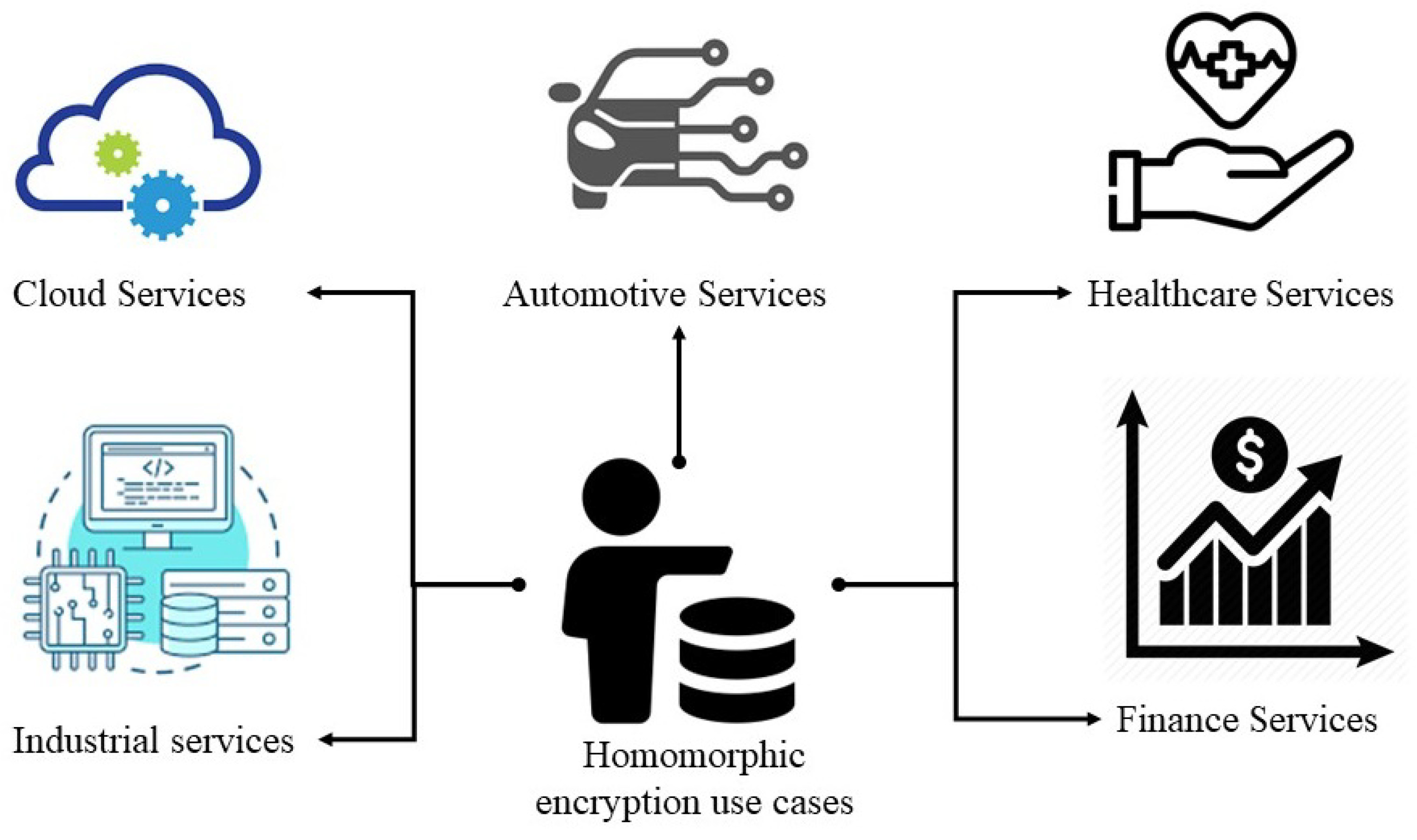
Entropy | Free Full-Text | Towards Secure Big Data Analysis via Fully Homomorphic Encryption Algorithms

Figure 5 from Privacy Preserving System Using Attribute Based Encryption for e-Health Cloud | Semantic Scholar

Cryptography Use Cases - CompTIA Security+ SY0-501 - 6.1 - Professor Messer IT Certification Training Courses
![A review of Comparative Study of Rc4a and MD5 Security Algorithm to Guarantee Confidentiality and Integrity [Part 2] — Steemit A review of Comparative Study of Rc4a and MD5 Security Algorithm to Guarantee Confidentiality and Integrity [Part 2] — Steemit](https://steemitimages.com/640x0/https://cdn.steemitimages.com/DQmNkZ6GnZmCtcKbzNMsR3CG9E2shEpT1iYEkqkt2as2hR1/2.PNG)
A review of Comparative Study of Rc4a and MD5 Security Algorithm to Guarantee Confidentiality and Integrity [Part 2] — Steemit

Figure 1 from Comparison of Implementation Tiny Encryption Algorithm (TEA) and Advanced Encryption Standard (AES) Algorithm on Android Based Open Source Cryptomator Library | Semantic Scholar

Parquet Modular Encryption: The New Open Standard for Big Data Security Reaches a Milestone • CyberKit4SME Project
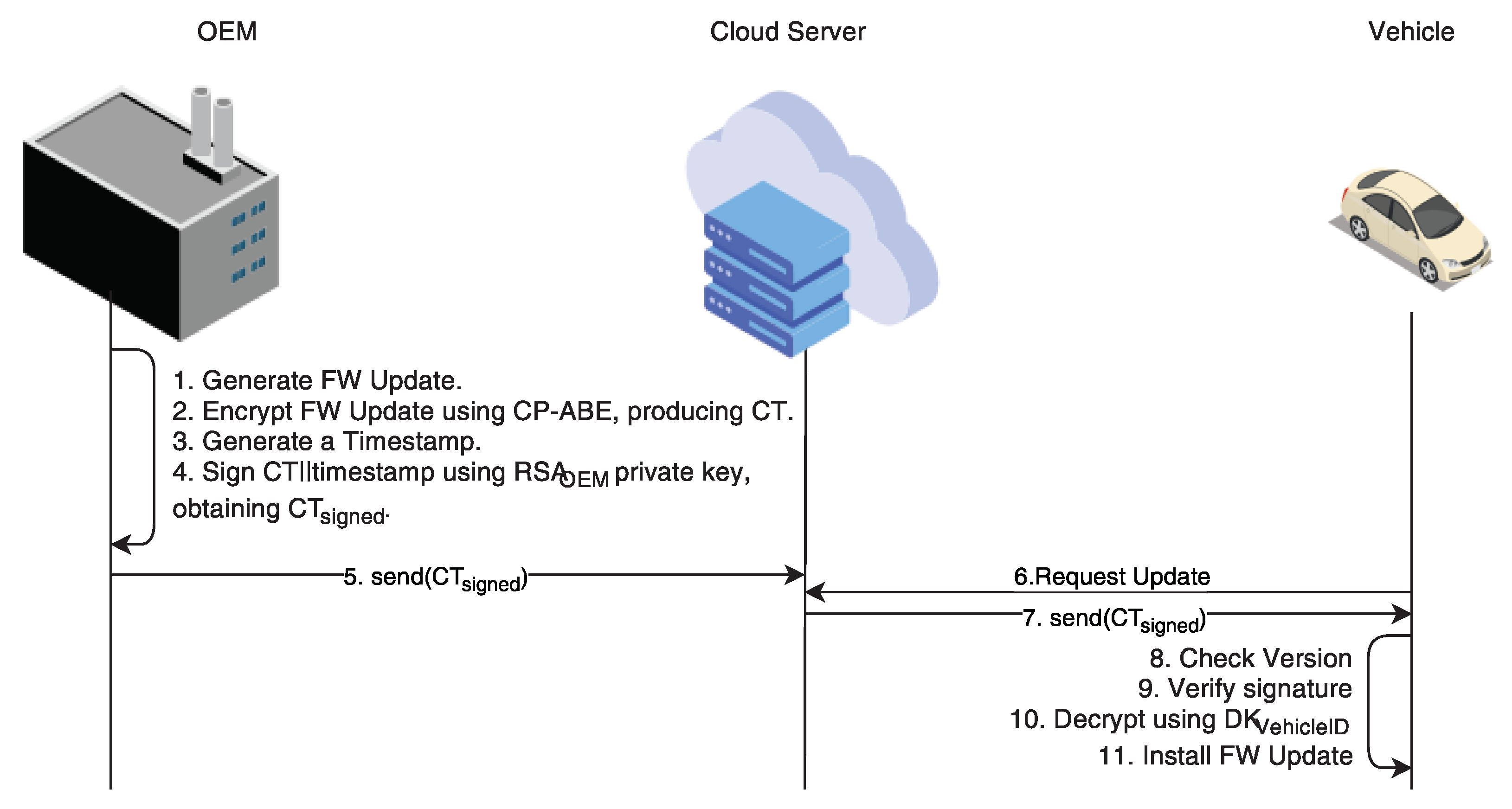
![MS-STOROD]: Encrypted File Access Control and Encryption | Microsoft Learn MS-STOROD]: Encrypted File Access Control and Encryption | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-storod/ms-storod_files/image007.png)