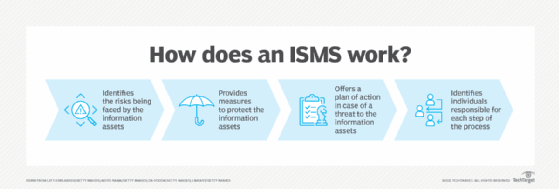
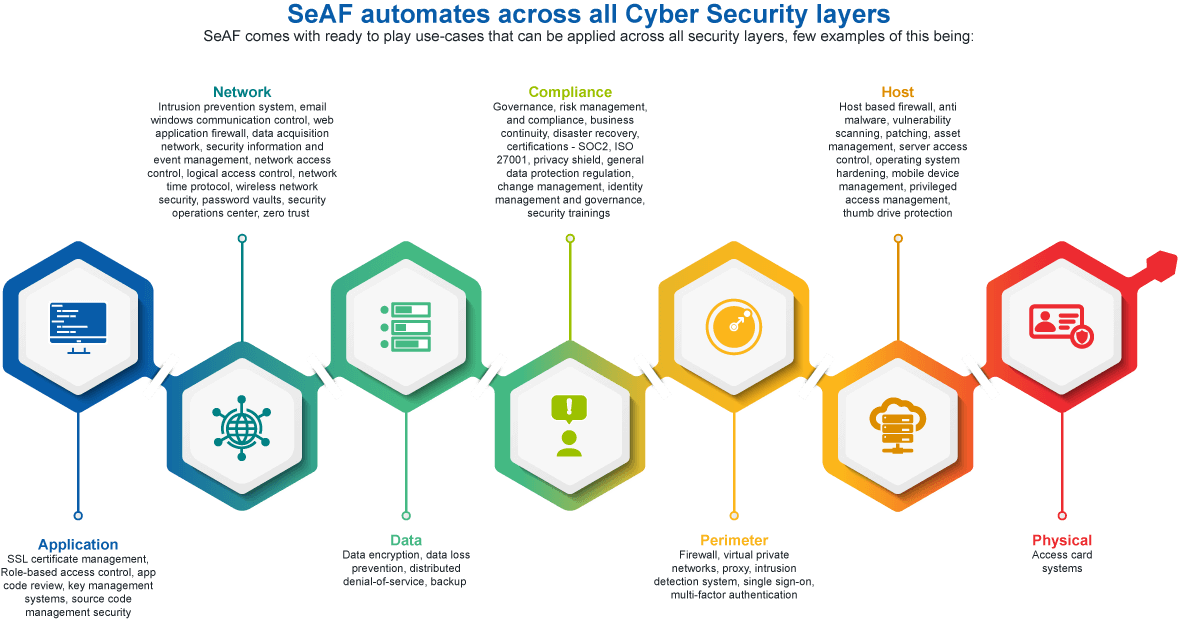
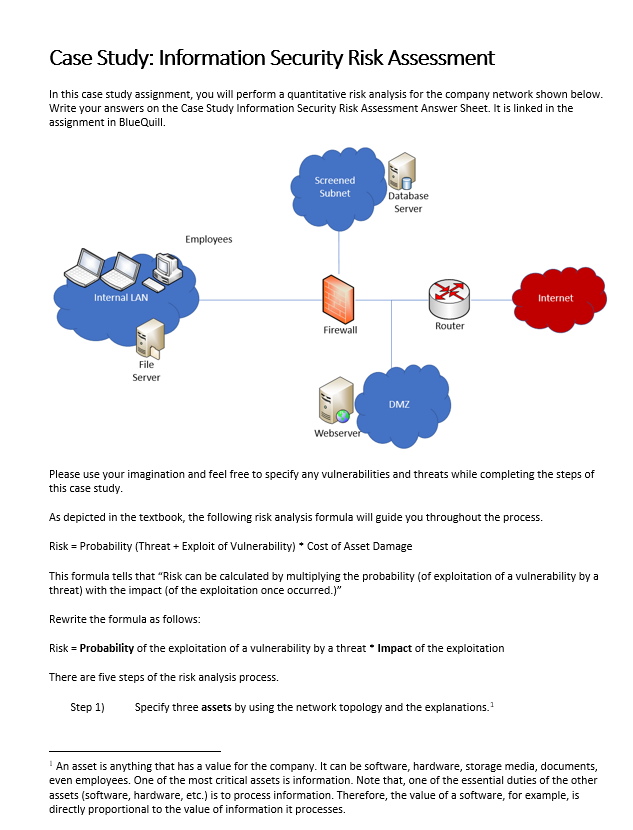
ISO/IEC DIS 24392(en), Cybersecurity — Security reference model for industrial Internet platform (SRM- IIP)
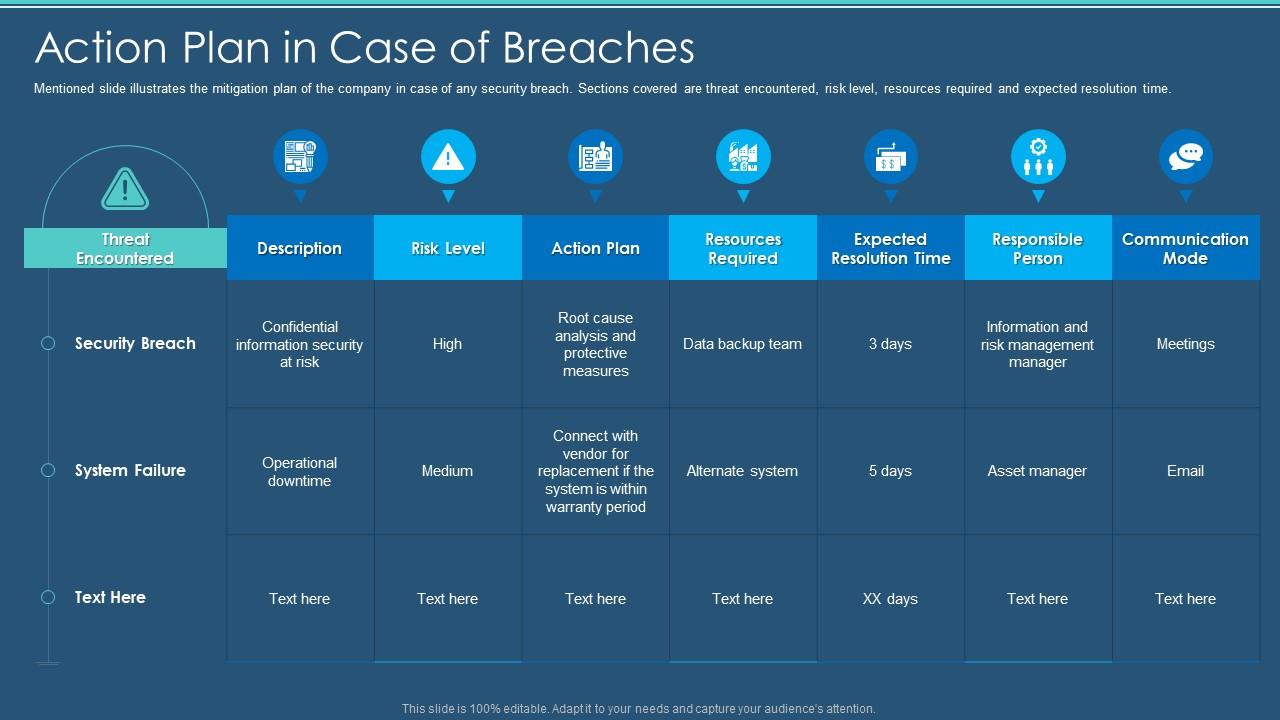
Information Security Program Cybersecurity Action Plan In Case Of Breaches | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
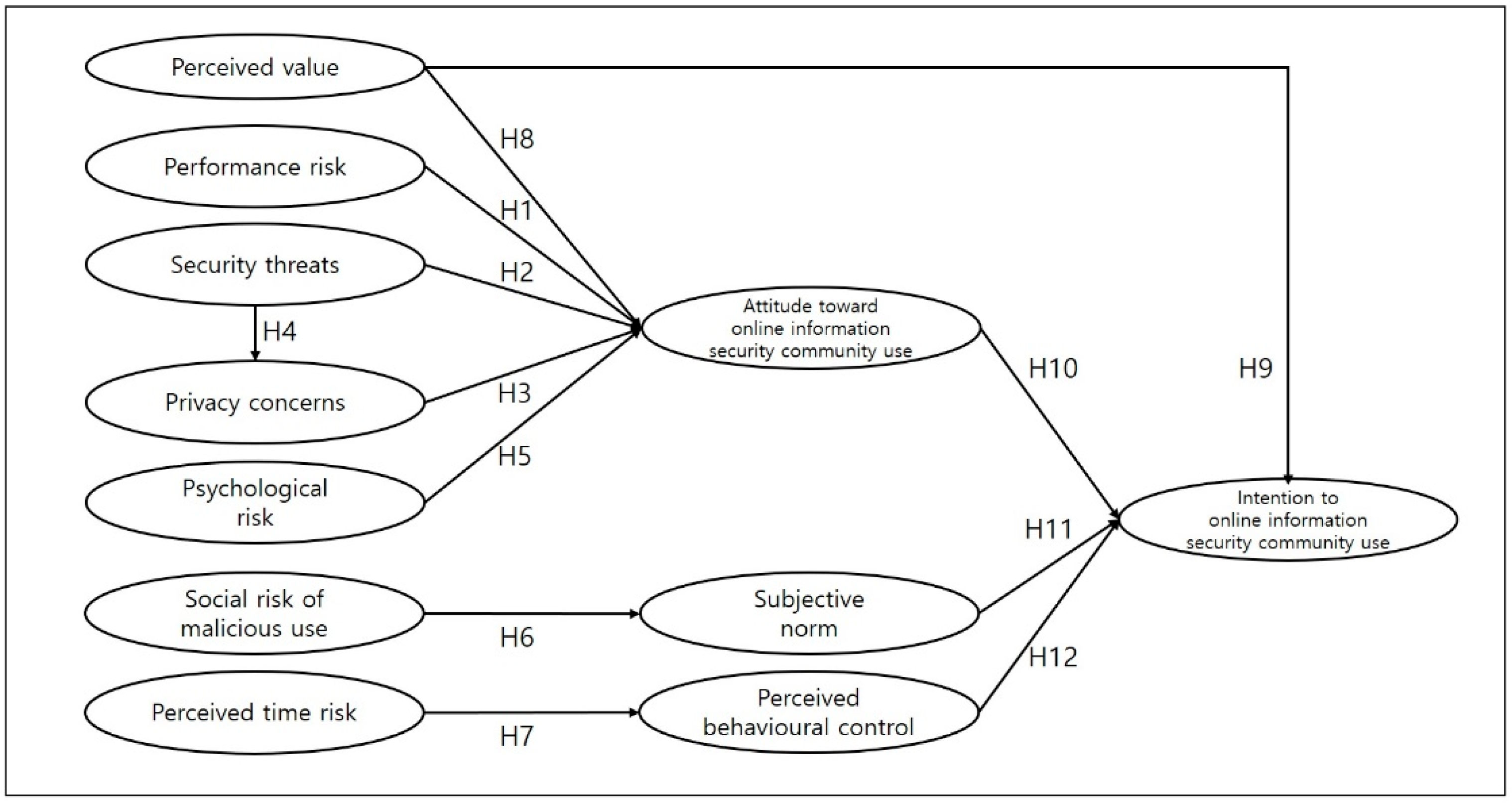
Sustainability | Free Full-Text | The Impact of Potential Risks on the Use of Exploitable Online Communities: The Case of South Korean Cyber-Security Communities