How to BYOK (bring your own key) to AWS KMS for less than $15.00 a year using AWS CloudHSM | AWS Security Blog

Figure 1 from Software size measurement of knowledge management portal with use case point | Semantic Scholar

Generic AWS KMS Key Deployments. ACM.17 Creating a reusable KSM Key… | by Teri Radichel | Cloud Security | Medium

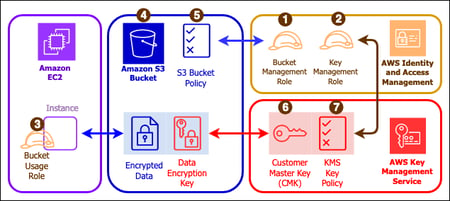
How to use KMS and IAM to enable independent security controls for encrypted data in S3 | AWS Security Blog