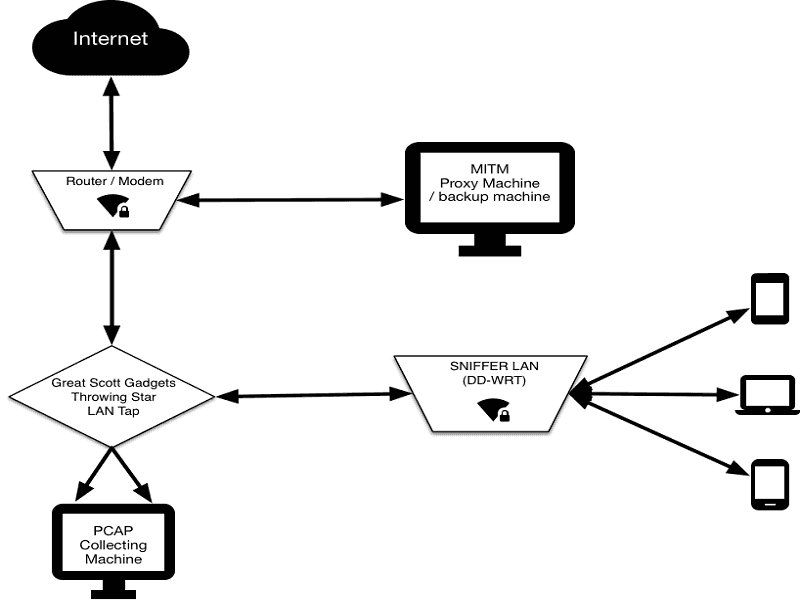
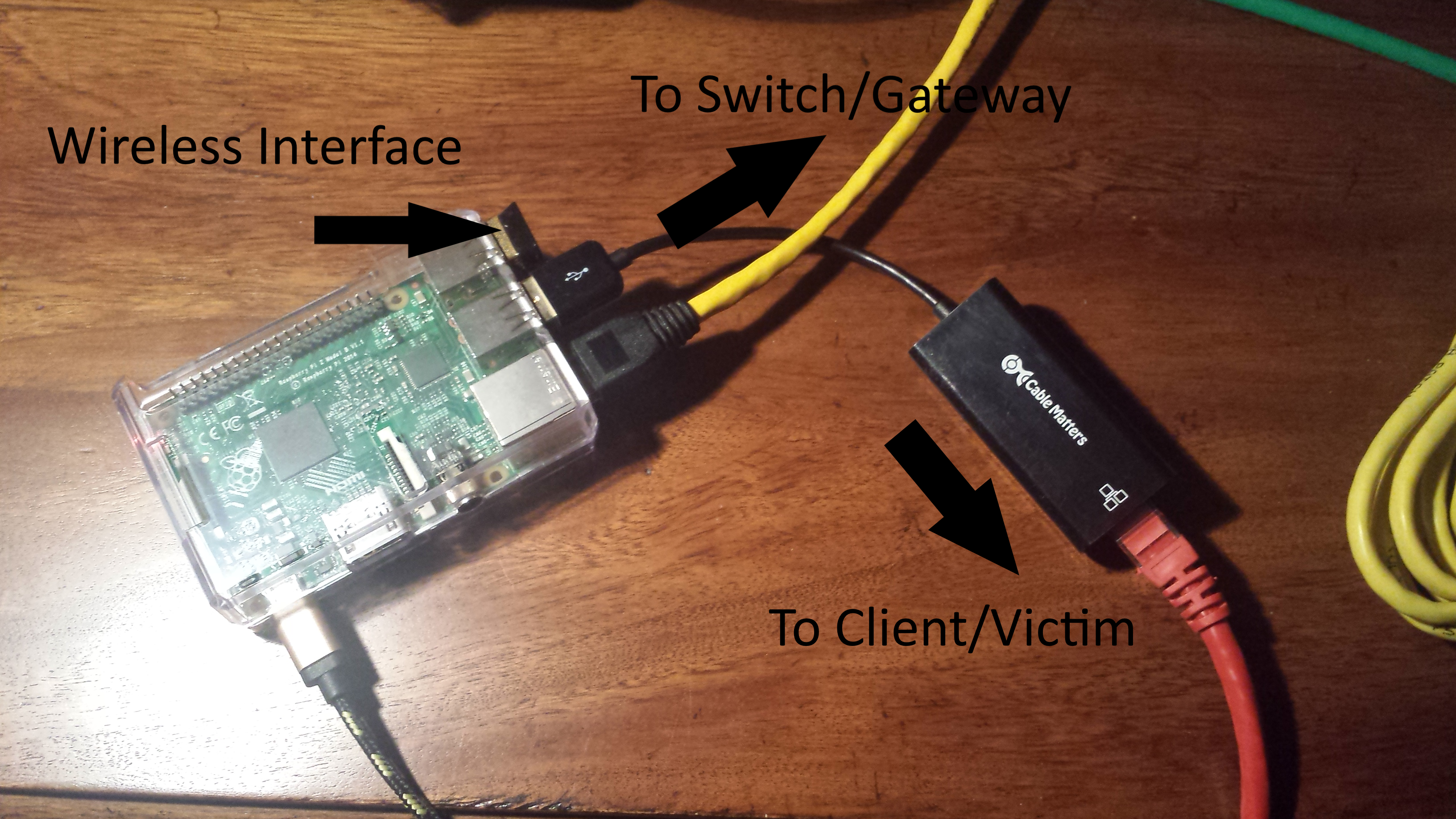
How to Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket « Null Byte :: WonderHowTo
GitHub - unknwncharlie/Int3rcept0r: Raspberry Pi Zero USB to Ethernet adapter MITM Gadget similar to the Lan Turtle

Wie kann das Netzwerkanalyse Programm Ettercap für eine MITM-Attacke (ARP-Spoofing) auf dem Raspberry Pi installiert werden? – Wenzlaff.de – Rund um die Programmierung

How to Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket « Null Byte :: WonderHowTo





![Build a Pumpkin Pi — A Rogue AP & MitM Framework That Fits in Your Pocket [Tutorial] - YouTube Build a Pumpkin Pi — A Rogue AP & MitM Framework That Fits in Your Pocket [Tutorial] - YouTube](https://i.ytimg.com/vi/tIM-kdmKhnE/mqdefault.jpg)
![Build a Pumpkin Pi — A Rogue AP & MitM Framework That Fits in Your Pocket [Tutorial] - YouTube Build a Pumpkin Pi — A Rogue AP & MitM Framework That Fits in Your Pocket [Tutorial] - YouTube](https://i.ytimg.com/vi/tIM-kdmKhnE/maxresdefault.jpg)