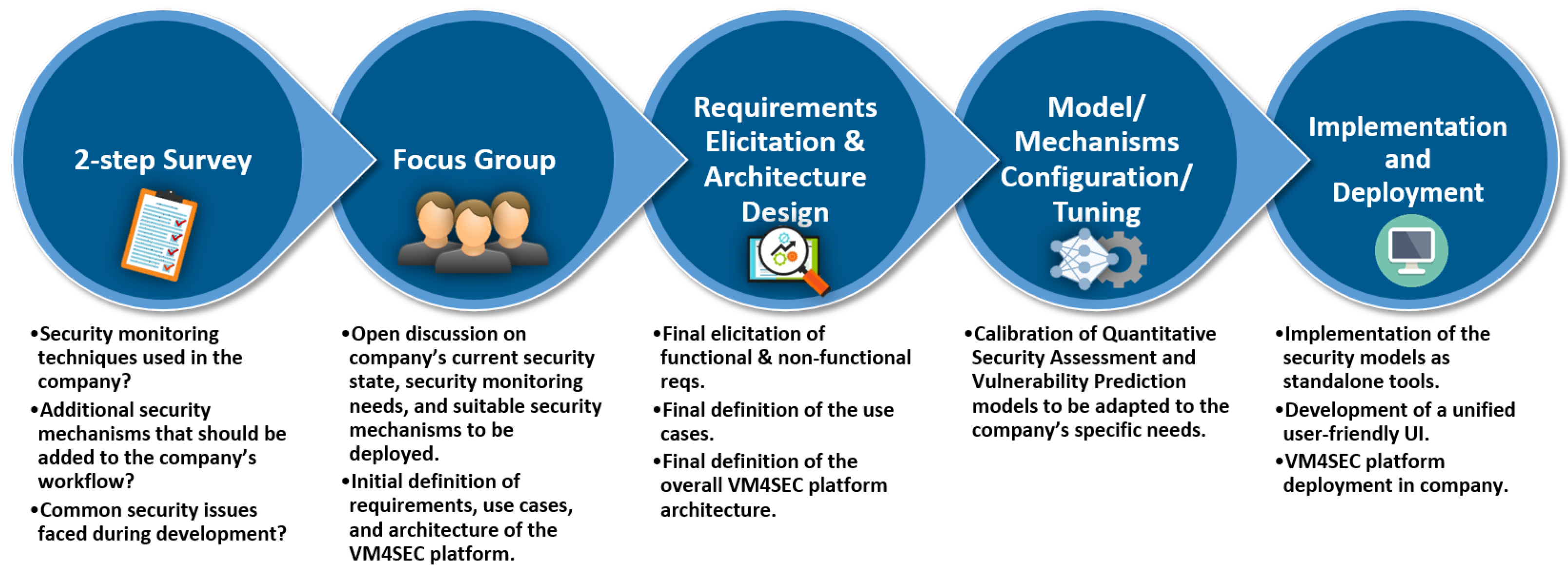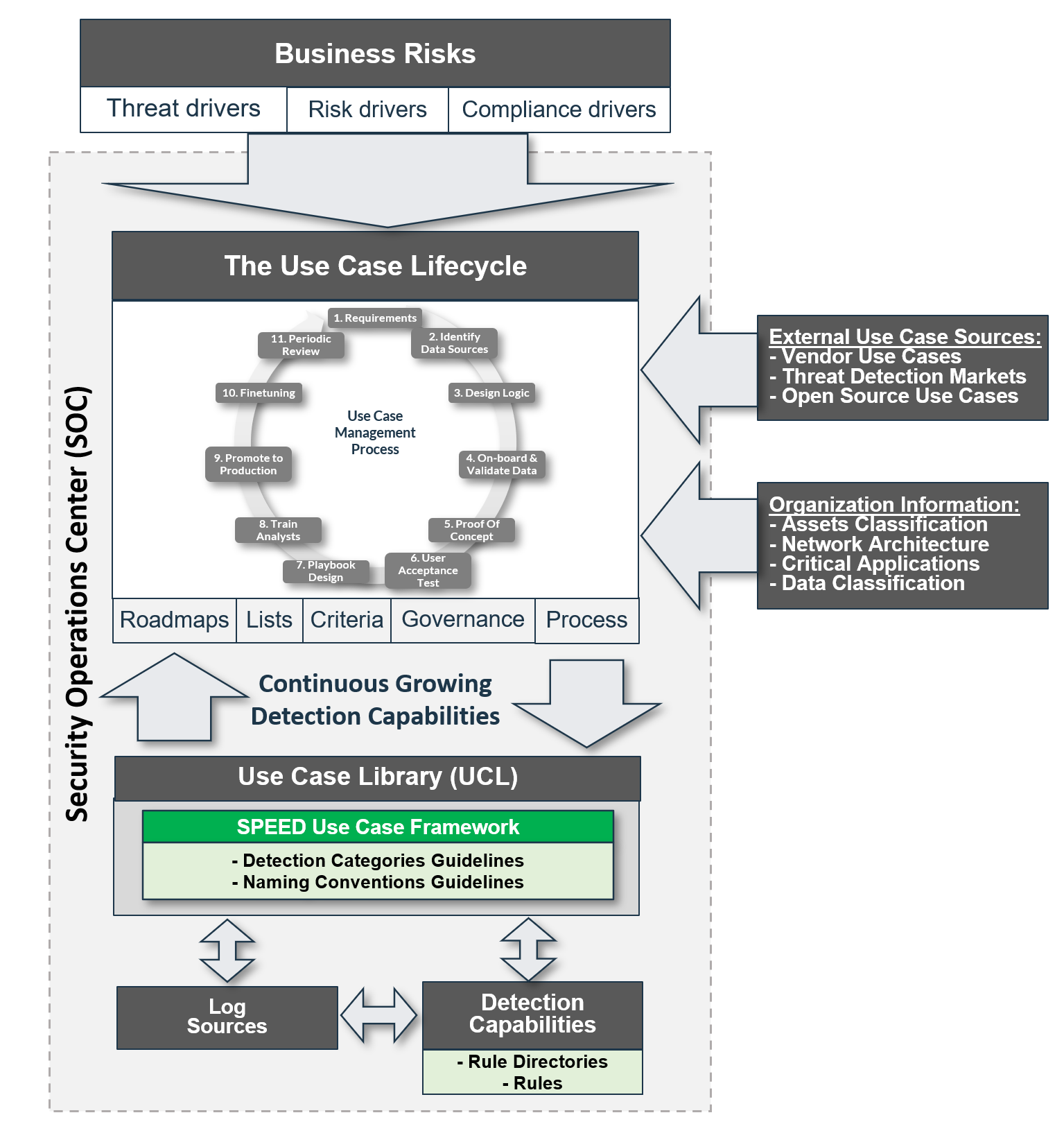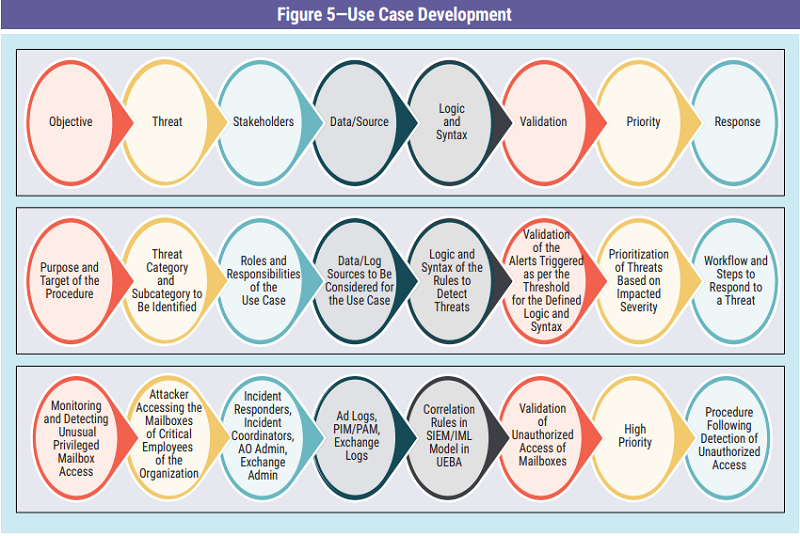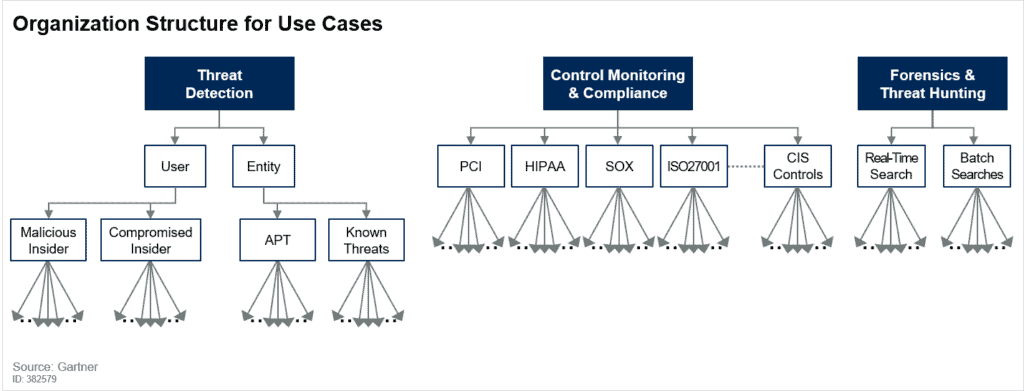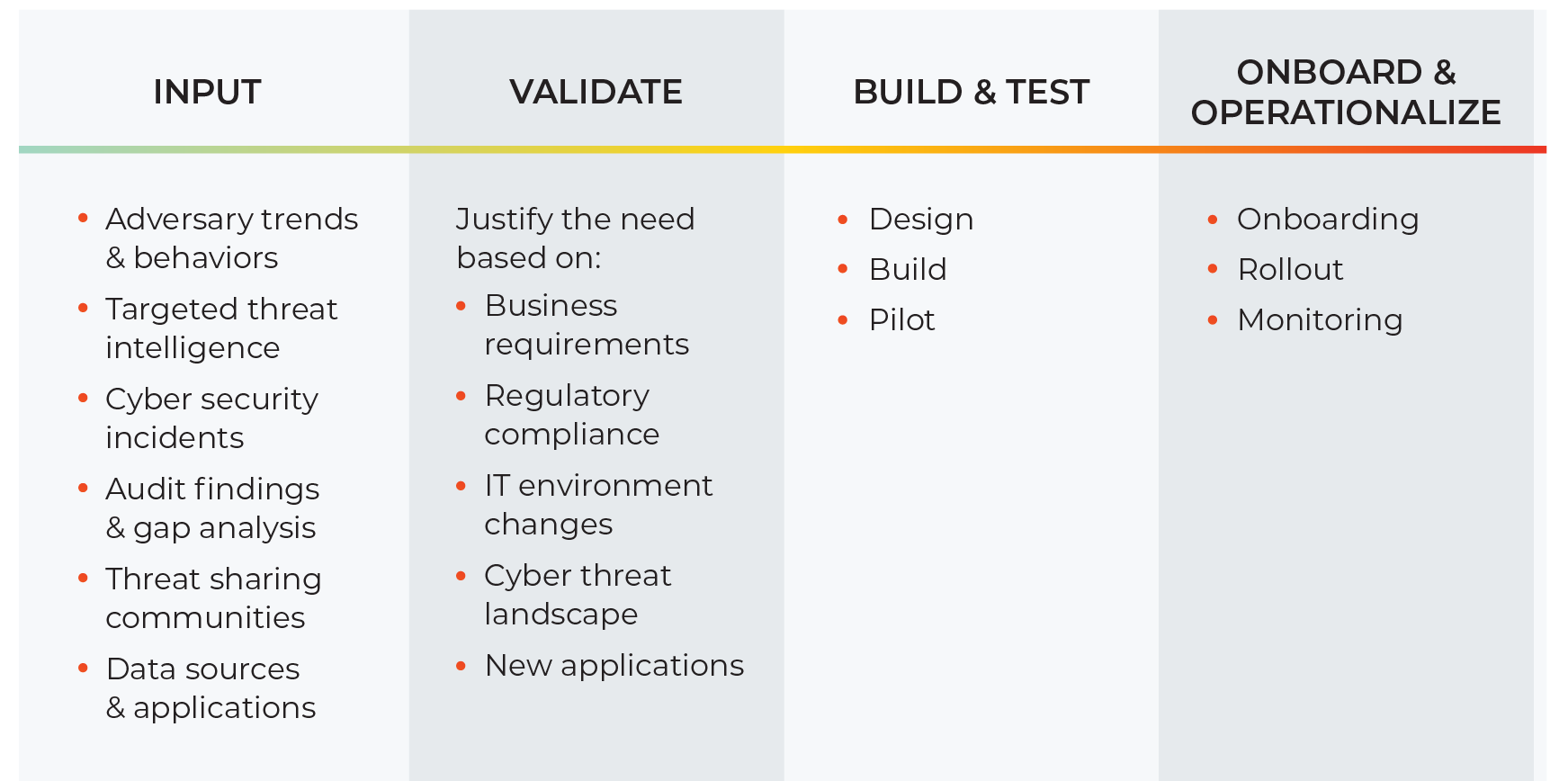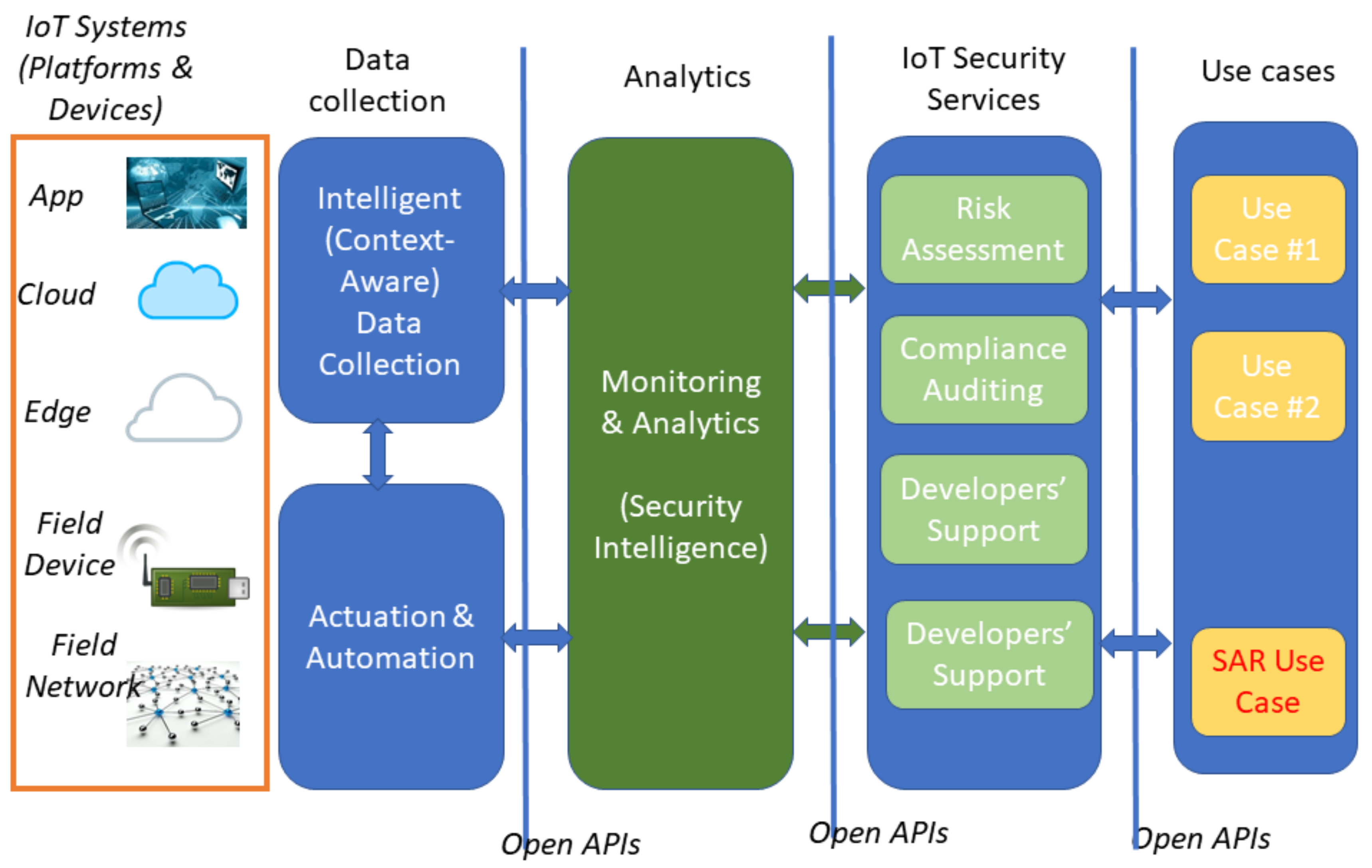
Sensors | Free Full-Text | Enabling Security Services in Socially Assistive Robot Scenarios for Healthcare Applications

Application Use Case Below will explain Figure 1 and Figure 2 how it... | Download Scientific Diagram
Cloud Security Monitoring Use Cases Ppt Powerpoint Presentation Slides Example Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates