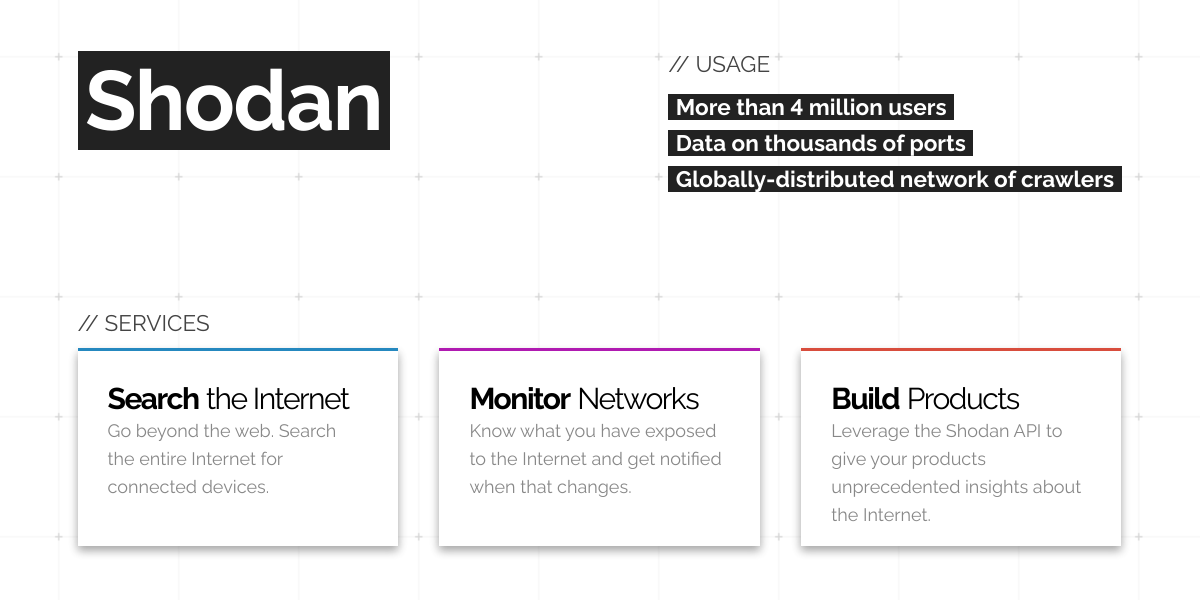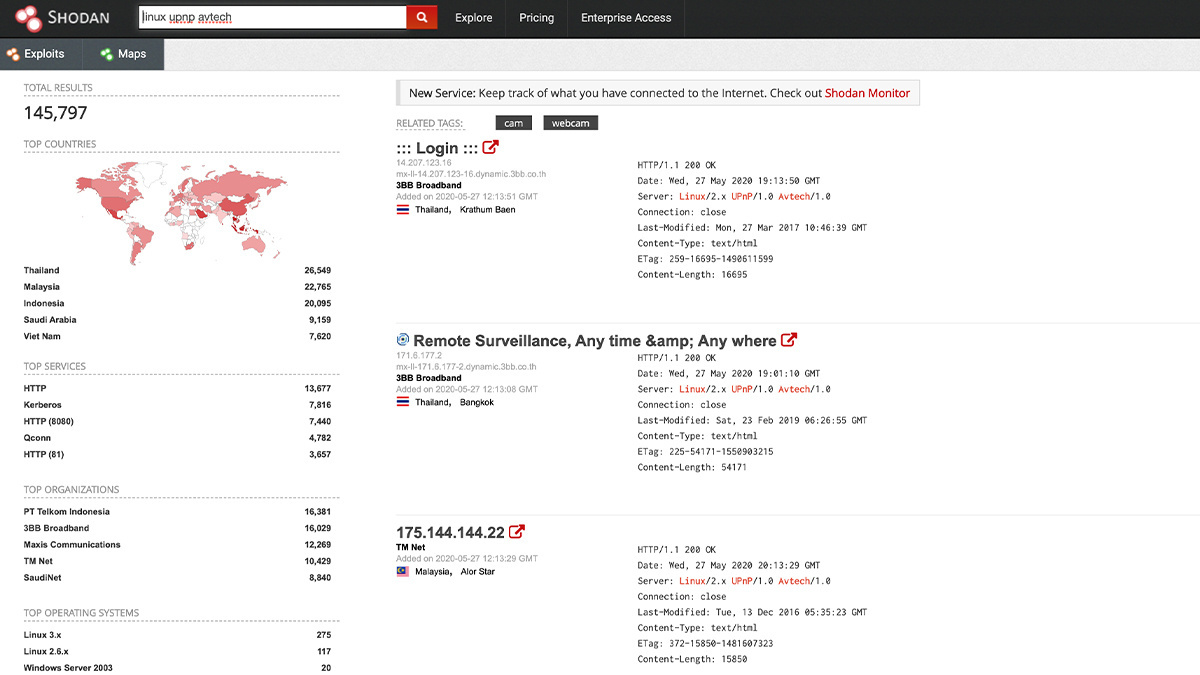
Shodan founder John Matherly on IoT security, dual-purpose hacking tools, and information overload | The Daily Swig
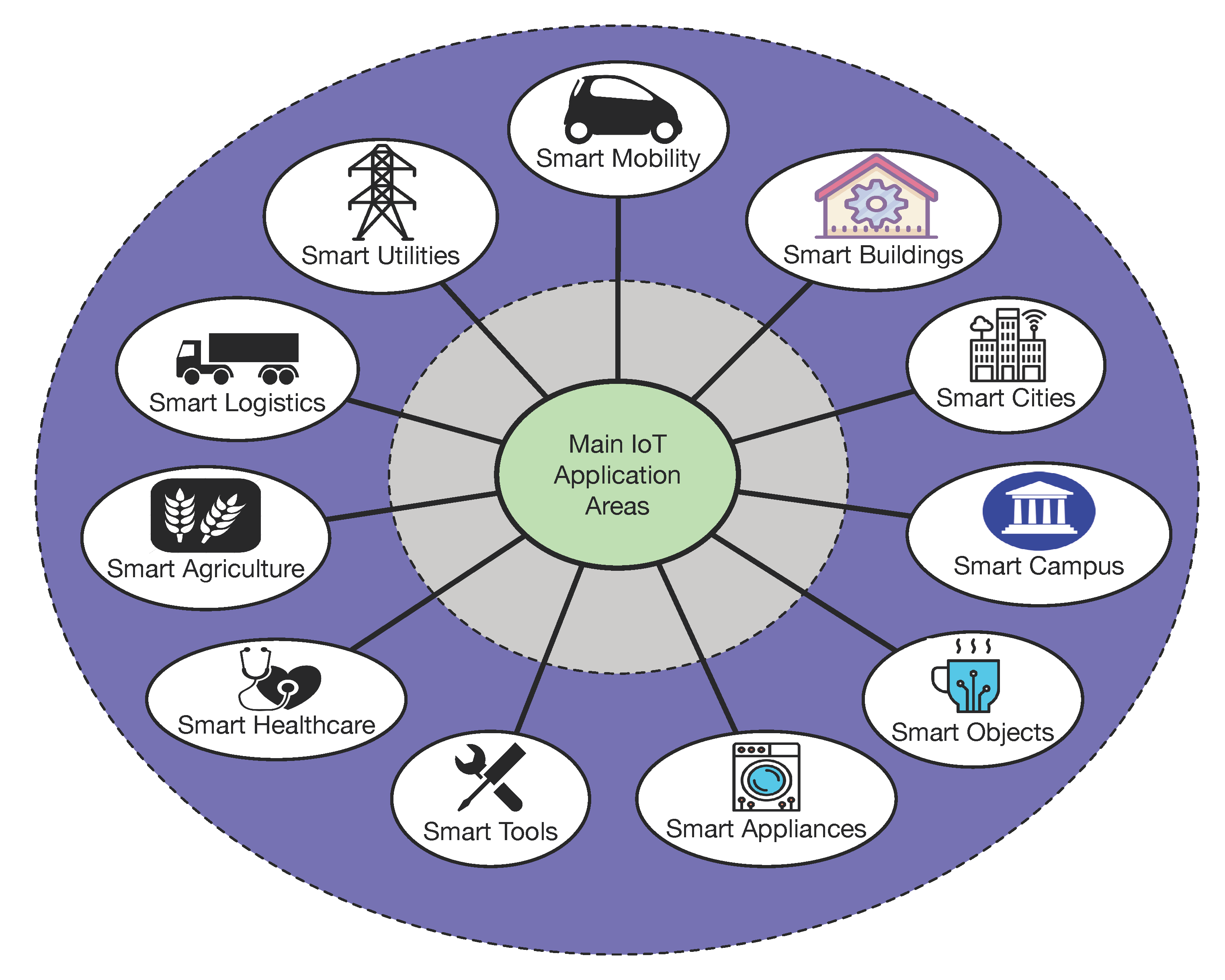
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
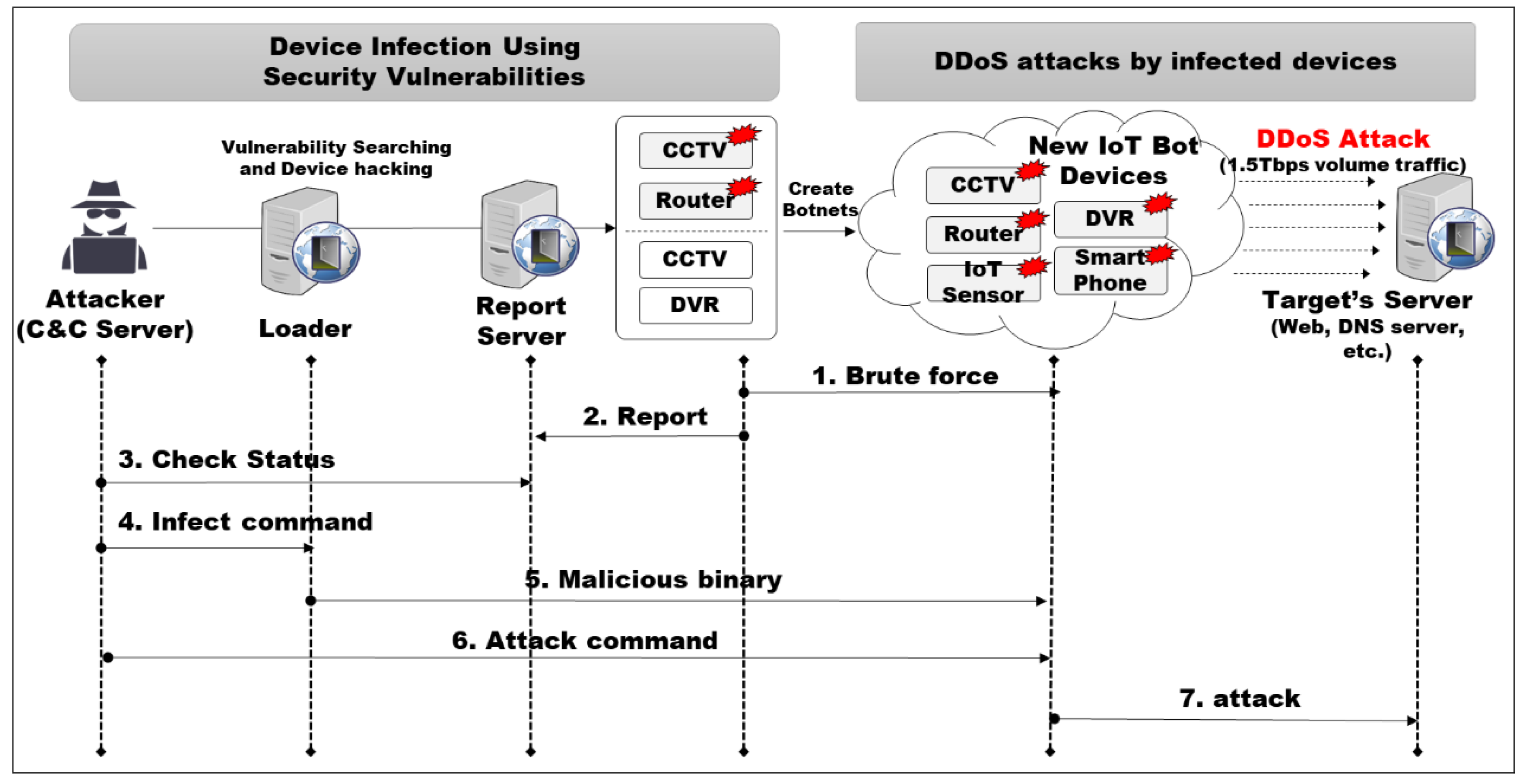
Symmetry | Free Full-Text | An Intelligent Improvement of Internet-Wide Scan Engine for Fast Discovery of Vulnerable IoT Devices

Shodan on Twitter: "More than 18% of Exchange servers remain unpatched for the ProxyShell vulnerability. Nearly 40% are vulnerable to CVE-2021-31206: https://t.co/7yetz9GoJw https://t.co/0r2AOQsibB" / Twitter

ShoVAT: Shodan‐based vulnerability assessment tool for Internet‐facing services - Genge - 2016 - Security and Communication Networks - Wiley Online Library


![Shodan Command Line a Step by Step Walkthrough - HackingPassion.com : root@HackingPassion.com-[~] Shodan Command Line a Step by Step Walkthrough - HackingPassion.com : root@HackingPassion.com-[~]](https://hackingpassion.com/shodan-command-line-a-step-by-step-walkthrough/featured-image.png)
![What Is Shodan? How to Use It & How to Stay Protected [2023] What Is Shodan? How to Use It & How to Stay Protected [2023]](https://www.safetydetectives.com/wp-content/uploads/2021/04/what-is-shodan-1.png)
![Search for Vulnerable Devices Around the World with Shodan [Tutorial] - YouTube Search for Vulnerable Devices Around the World with Shodan [Tutorial] - YouTube](https://i.ytimg.com/vi/oDkg1zz6xlw/maxresdefault.jpg)
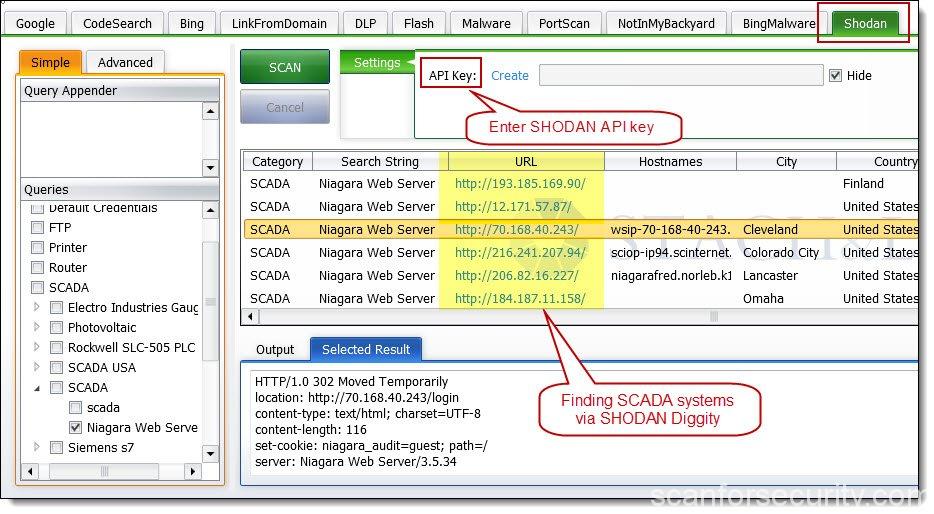
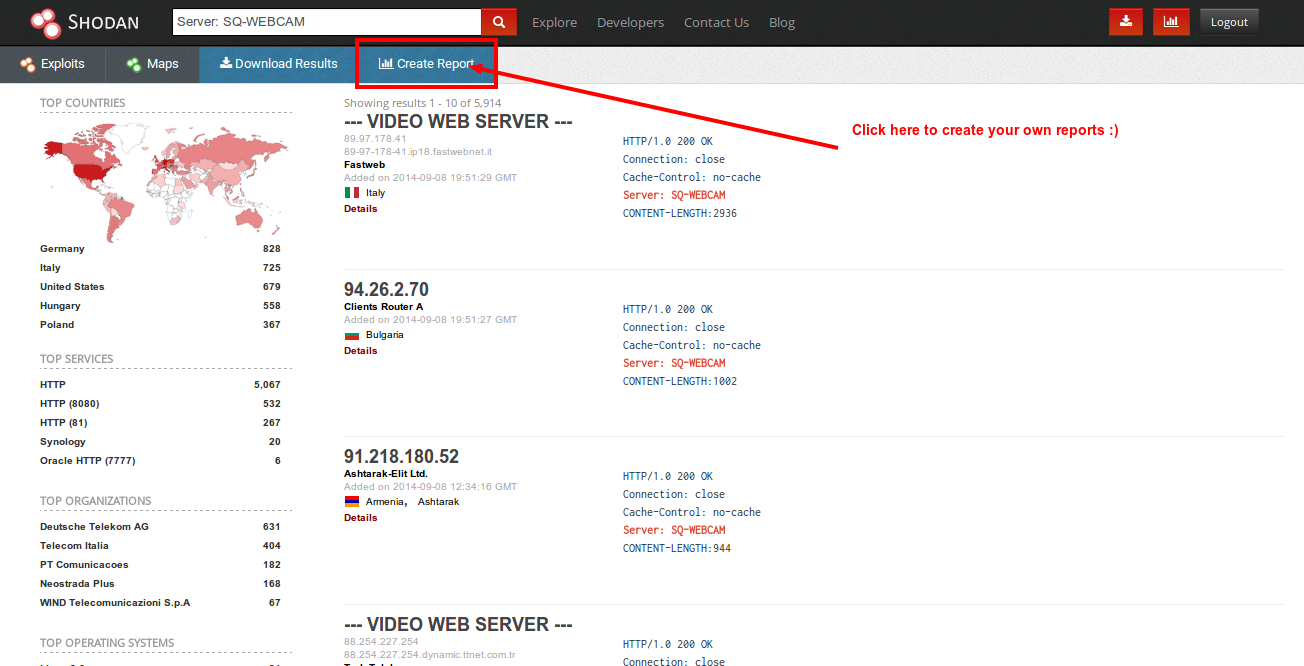

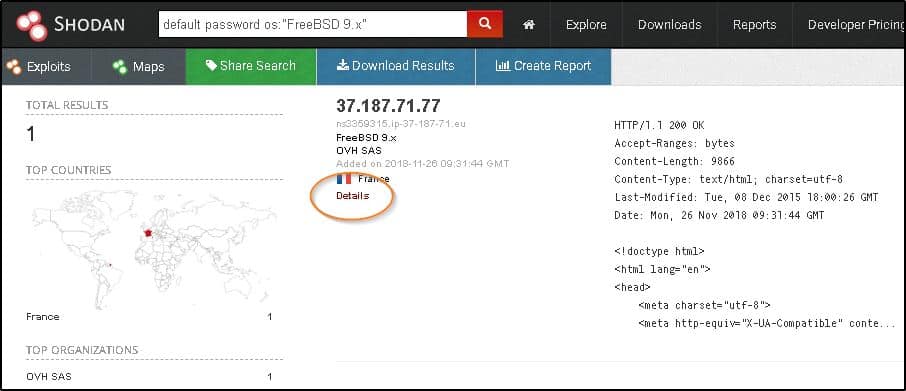
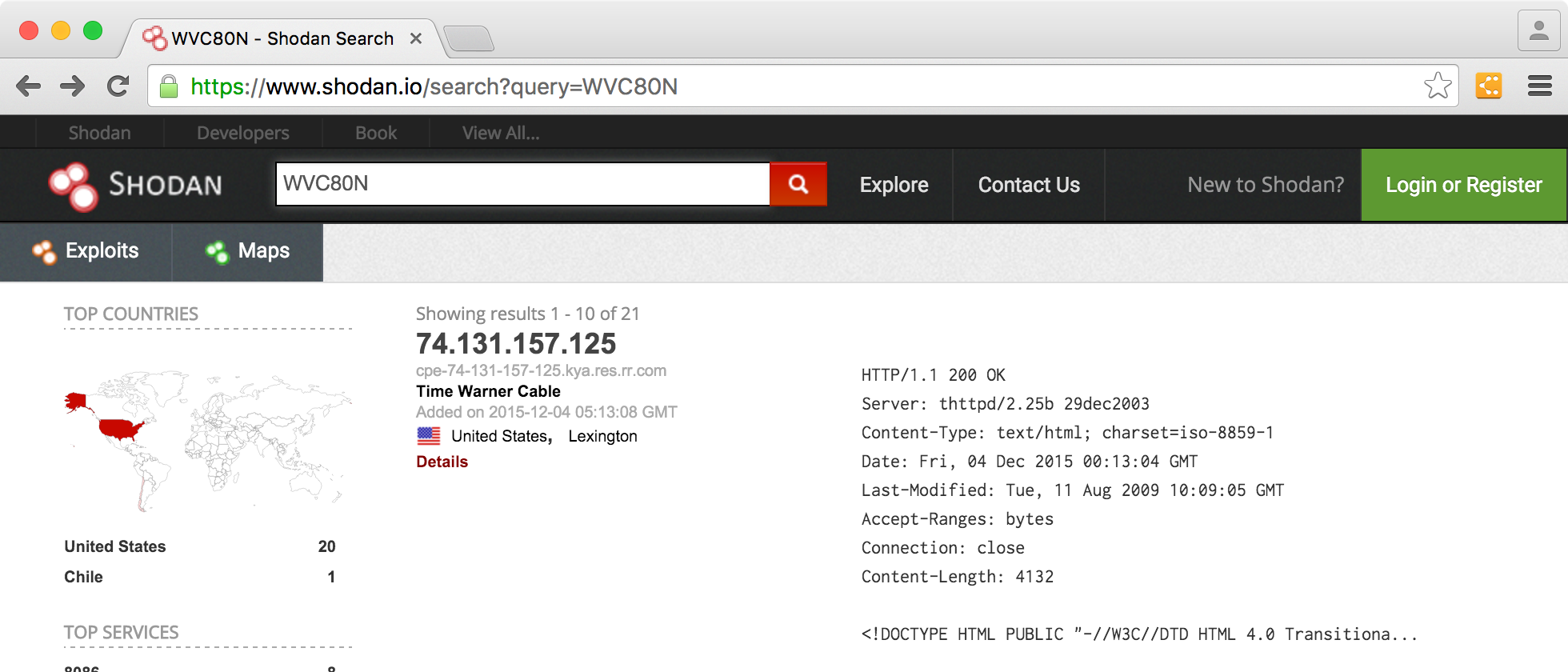

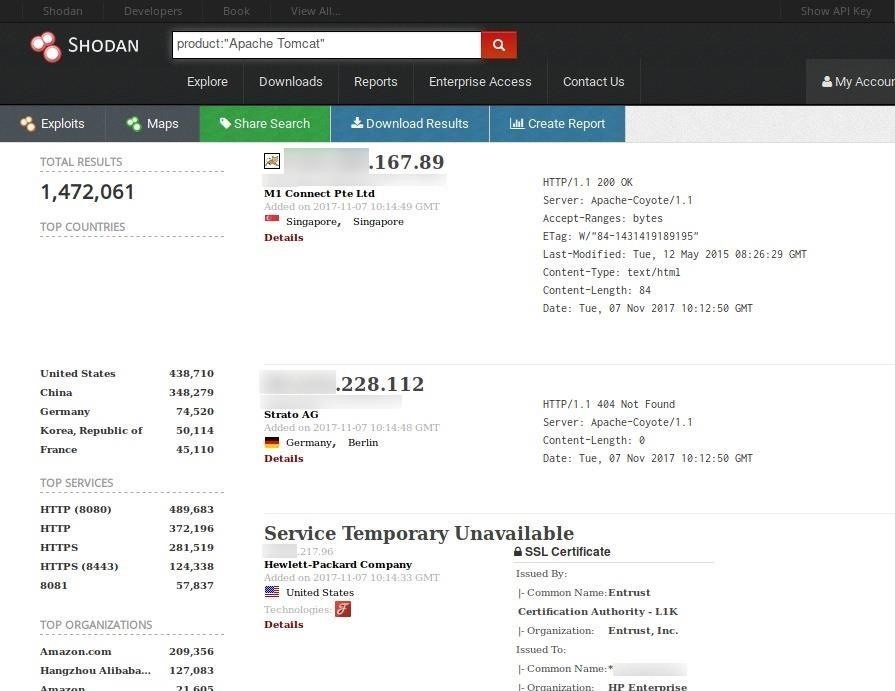
:quality(90)/images.vogel.de/vogelonline/bdb/1596900/1596944/original.jpg)