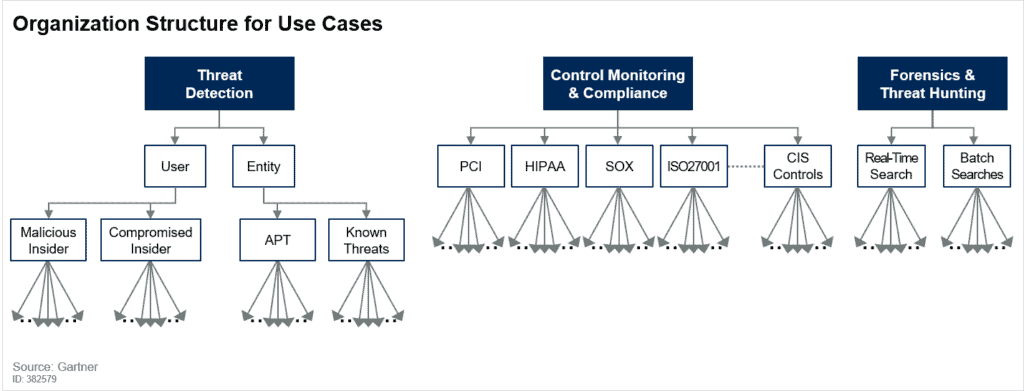
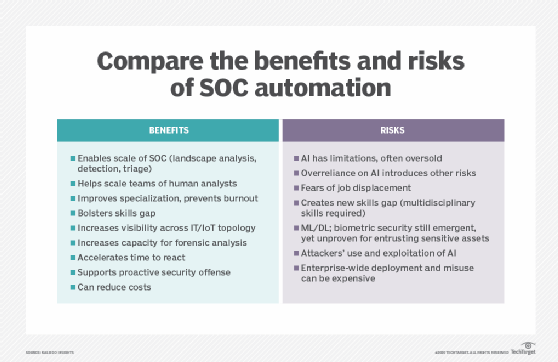
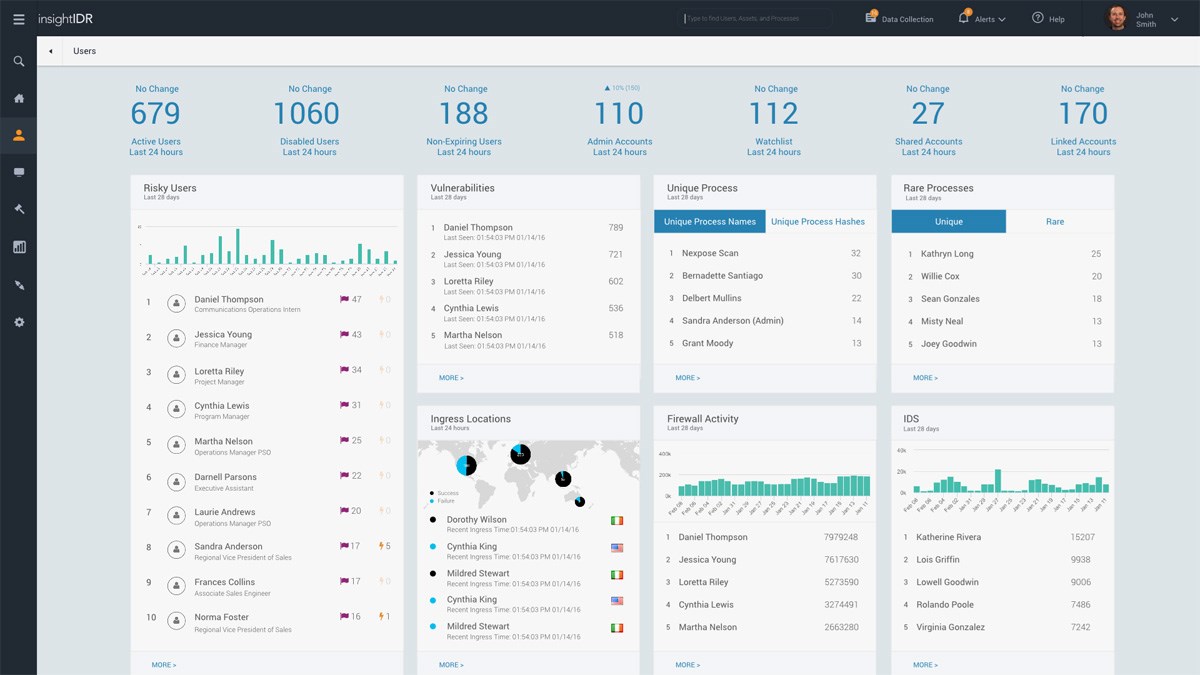
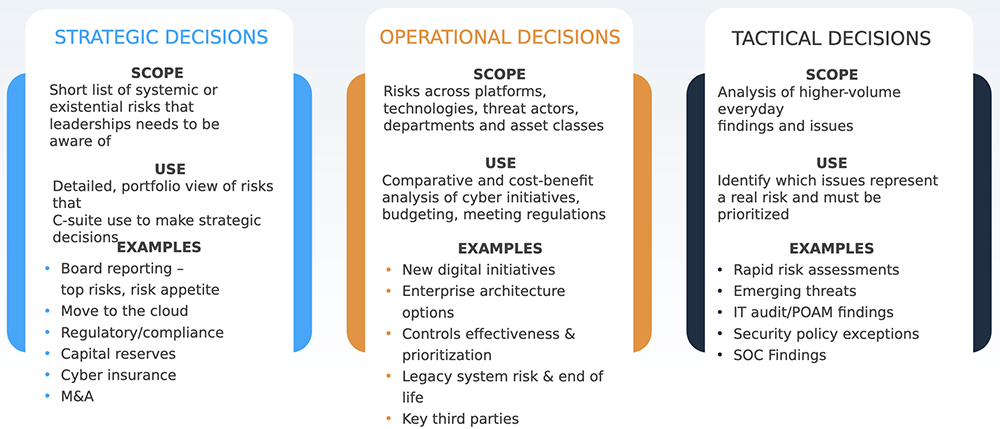
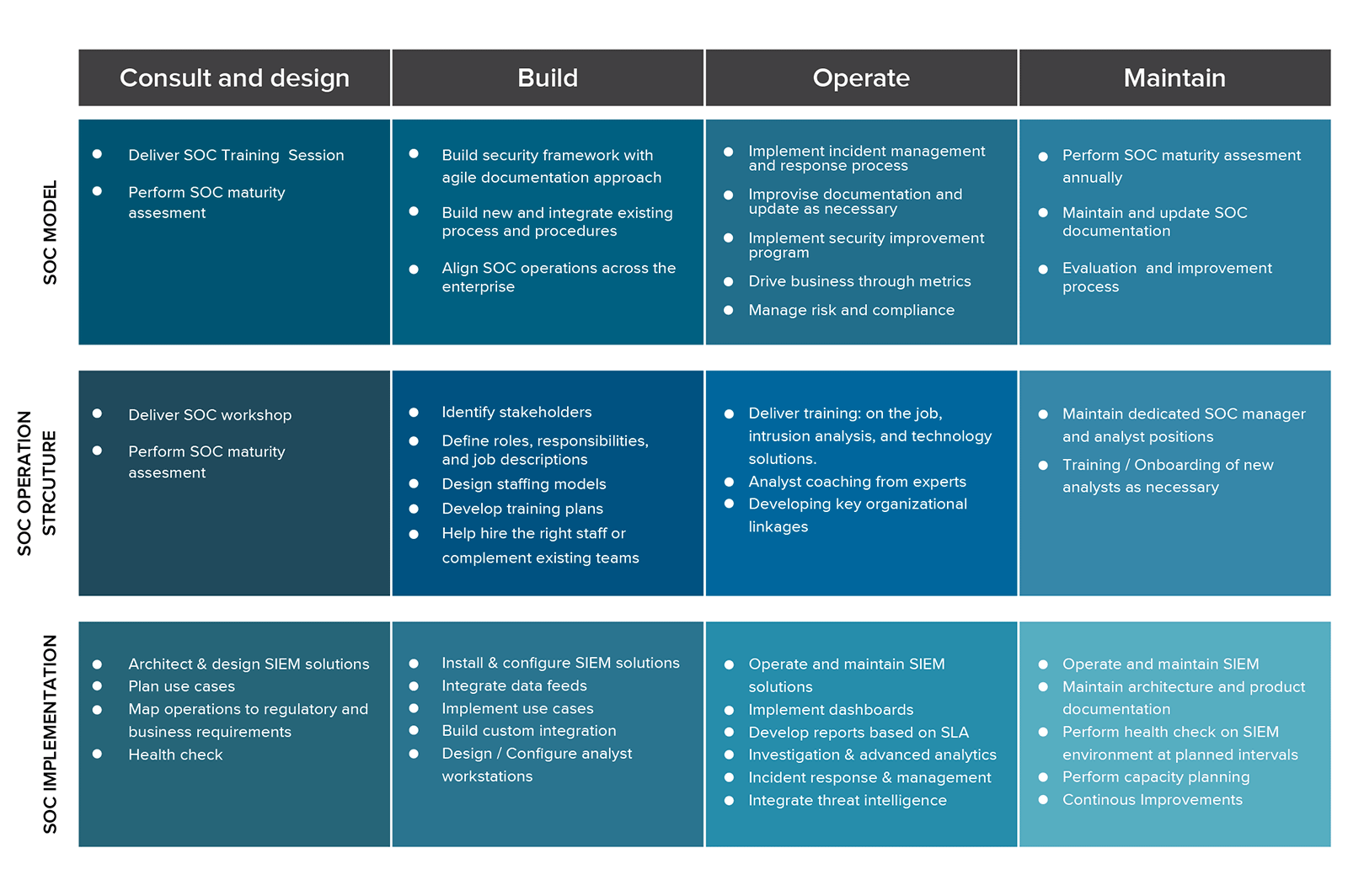
Demystifying the SOC, Part 5: The New SOC Maturity Model based on Outcomes | by Gorka Sadowski | Medium

Sensitive Data of 65,000+ Entities in 111 Countries Leaked due to a Single Misconfigured Data Bucket
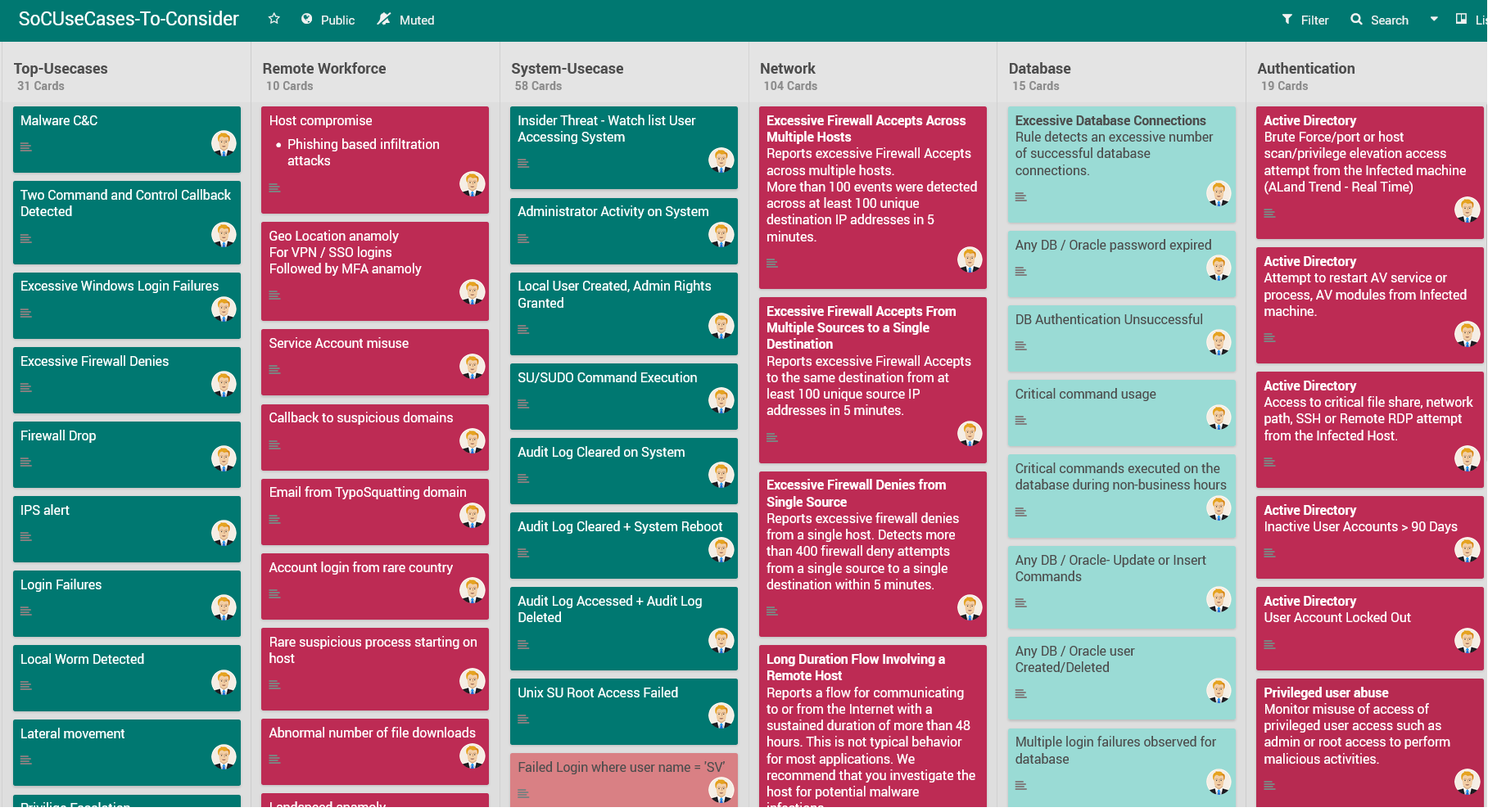
Use Case Library: a Cyber security collaboration platform for ArcSight, QRadar and Splunk - SOC Prime

Marcos Jaimovich en LinkedIn: 396 Use Cases & Siem Rules Code ready for use for Mitre Attacks Events…