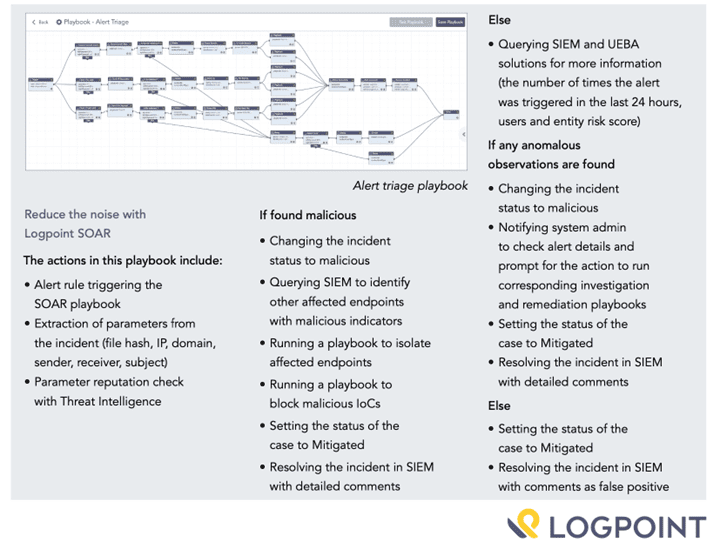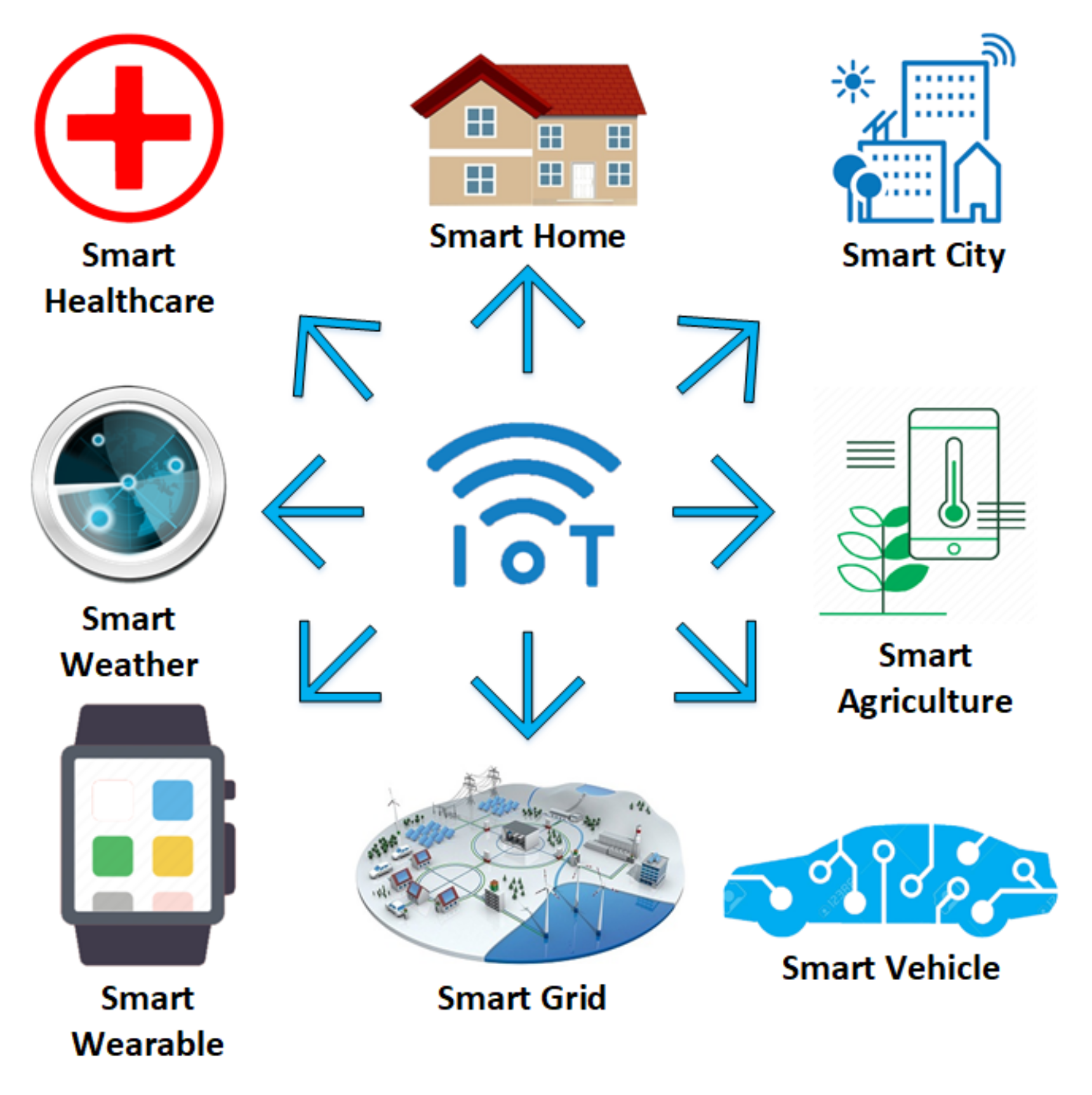
Sensors | Free Full-Text | Identifying and Mitigating Phishing Attack Threats in IoT Use Cases Using a Threat Modelling Approach
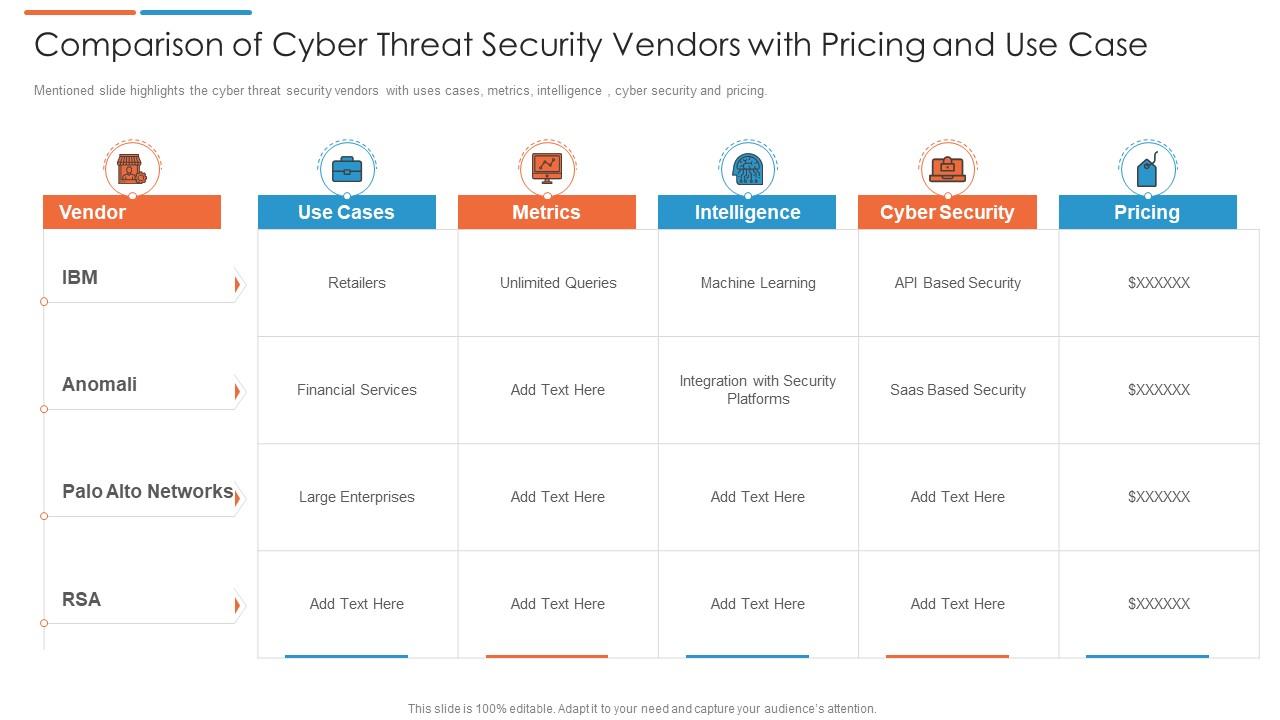
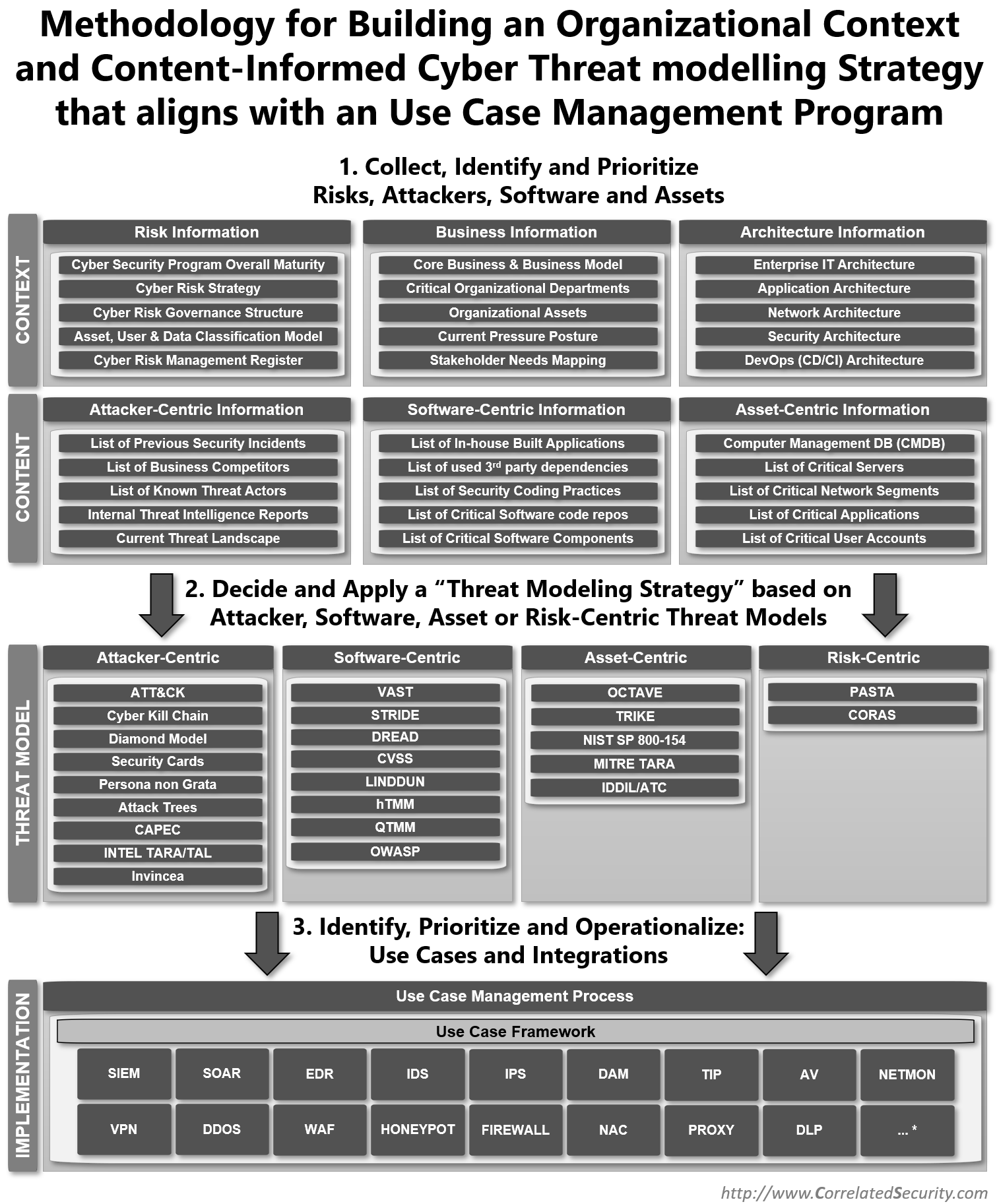
Comparison Of Cyber Threat Security Vendors With Pricing And Use Case | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
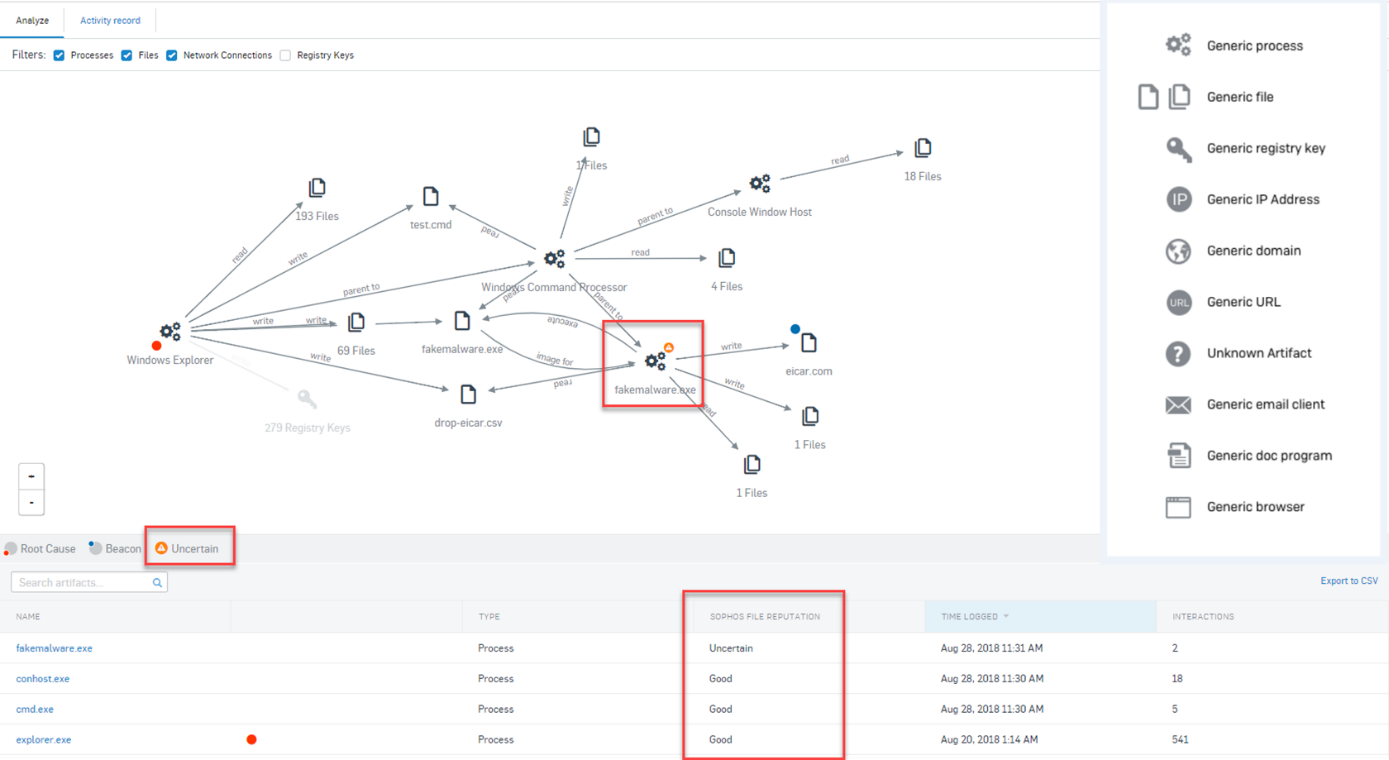
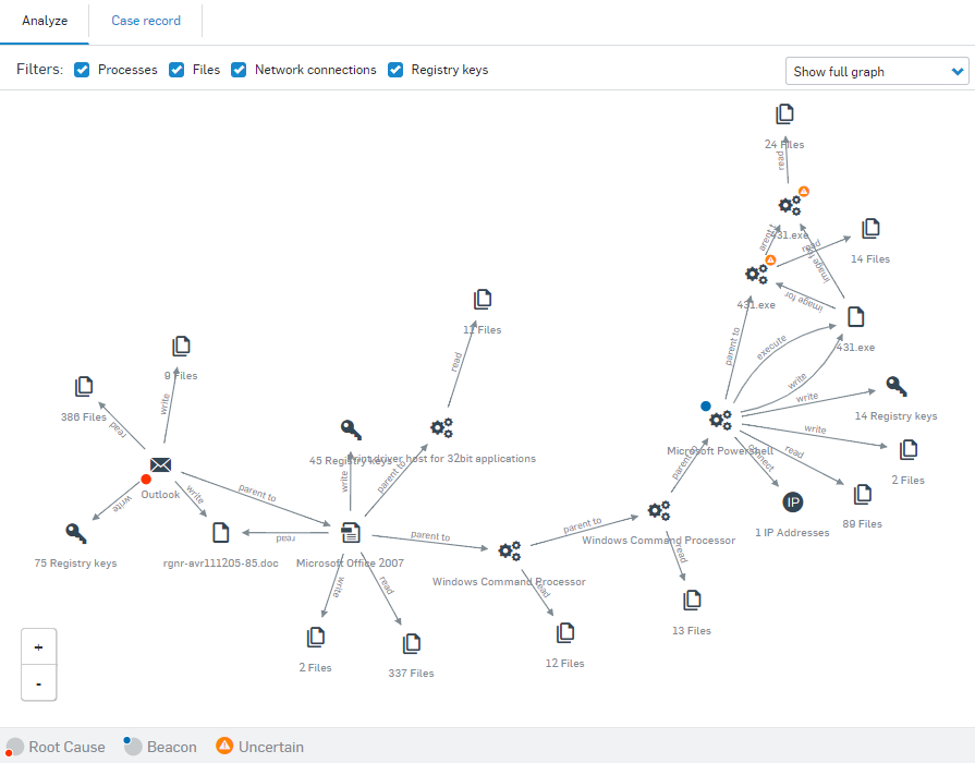
New and improved root cause analysis in Intercept X - Release Notes & News - Sophos Endpoint - Sophos Community

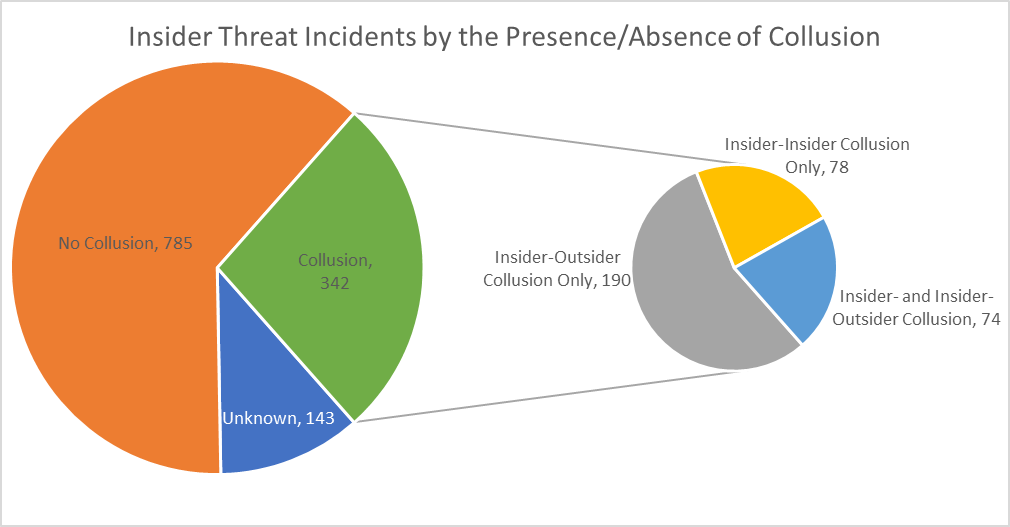
Blue Team Handbook: SOC, SIEM, and Threat Hunting Use Cases: A condensed field guide for the Security Operations team : Murdoch, GSE #99, Don: Amazon.de: Bücher
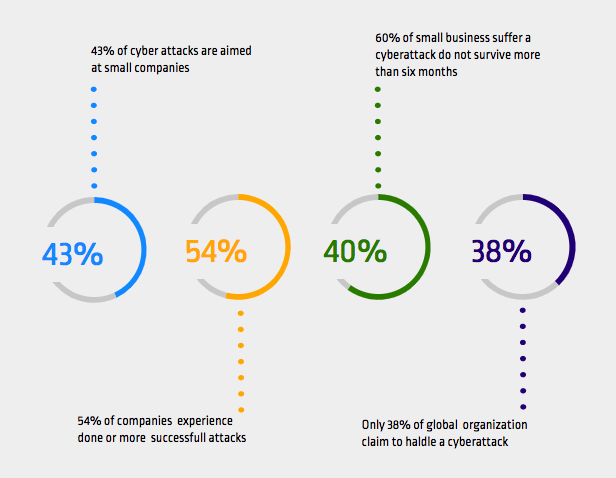
Top Threat Intelligence Use Cases for the E-commerce Industry-II - SOCRadar® Cyber Intelligence Inc.



![PDF] Developing Abuse Cases Based on Threat Modeling and Attack Patterns | Semantic Scholar PDF] Developing Abuse Cases Based on Threat Modeling and Attack Patterns | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b8692e2a9594eb37922303e8cfb9d9665af24940/3-Figure1-1.png)

![PDF] Developing Abuse Cases Based on Threat Modeling and Attack Patterns | Semantic Scholar PDF] Developing Abuse Cases Based on Threat Modeling and Attack Patterns | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b8692e2a9594eb37922303e8cfb9d9665af24940/5-Figure3-1.png)